If you want to know how many devices are connected on your network, the ping sweep method is utilized. The ping sweep is a scanning technique to identify the online hosts available on the network. Different techniques of the ping sweep discover a specific target alive hosts or all the hosts on a network.
Ping sweep can be performed using several tools, such as Nmap (Network Mapper), an open-source network discovery tool that sends packets to a network and analyzes the responses to check if the host is online. The Nmap utility is very flexible for port scanning, device detection, and vulnerability checking on a network.
This article discusses different techniques of the Nmap ping sweep with the help of the following supporting content:
- Install Nmap in Linux
- How to Use the Nmap Ping Sweep?
- Scans for Different Transfer Protocols
- Scan for a Specific Port
- Ping Scanning for Live Host
- IP Address Scanning
Let’s start with installing the ping sweep in Linux.
Install Nmap in Linux
To perform the ping sweep method with the Nmap tool; you must install it using the below command:
$ sudo apt install nmap -y
The Nmap utility is installed in the system.
How to Use the Nmap Ping Sweep?
The general command used to scan the ping is as follows:
$ nmap <ping-options> <ip-address>
- Nmap: It shows the Nmap utility is used.
- ping options: Replace it with specific ping options.
- IP address: Replace it with the targeted IP address or range of IP addresses that you want to discover.
The Nmap ping sweep allows the following scan types:
| -sn | Ping scan via ICMP, it’s not a port scanning, just a ping scan. |
| -PS | It scans via TCP SYN ping. |
| -PA | It scans via TCP ACK ping. |
| -PU | It scans via UDP ping. |
| -sL | It simply lists the targets to scan. |
| -Pn | Treats all the hosts online. |
Scans for Different Transfer Protocols
Several transfer protocols are used in networking for transferring files. This section will discuss using the Nmap tool to use different available protocols in Linux.
To ping sweep for TCP SYN protocol, the “PS” option is used. For instance, to scan the TCP SYN protocol to discover a specific IP address, the following command is utilized:
$ nmap -PS 192.168.100.46
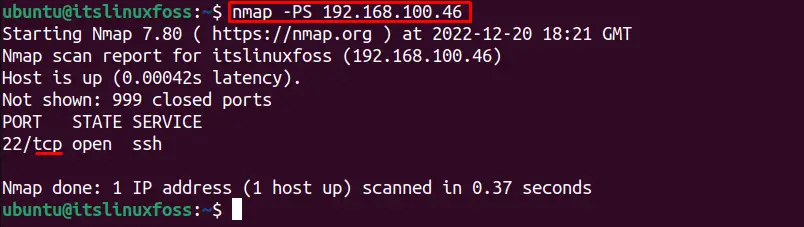
It will scan for the TCP SYN protocol only.
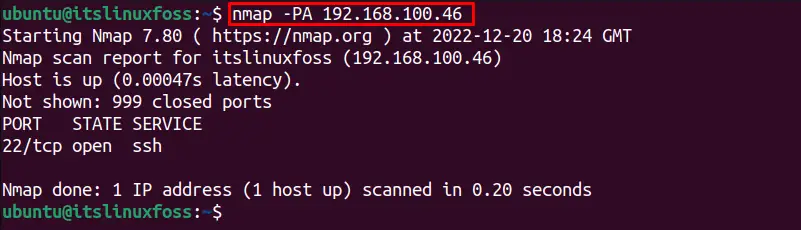
Similarly, to scan for TCP ACK protocol the “PA” option is used as done in the below command for the “192.168.100.46” IP address:
$ nmap -PA 192.168.100.46
To scan for UDP communication protocol, the “PU” option is utilized as shown below for the targeted IP address:
Note: The sudo permissions are required for UDP ping sweep.
$ nmap -PU 192.168.100.46
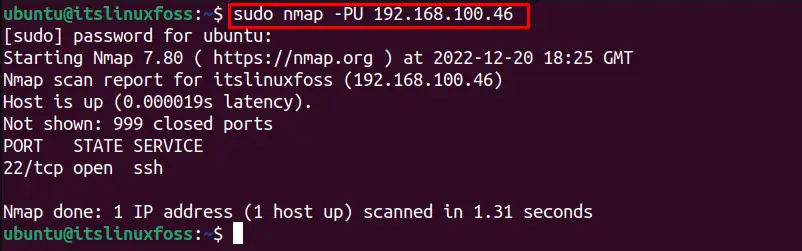
It shows that “192.168.100.46” is not connected via UDP.
Scan for a Specific Port
The Nmap ping sweep method can be used to scan for a specific port or several ports. For example, to discover the status of the “192.168.100.46” at port “80”, the following command is utilized:
$ nmap 192.168.100.46 -p 80
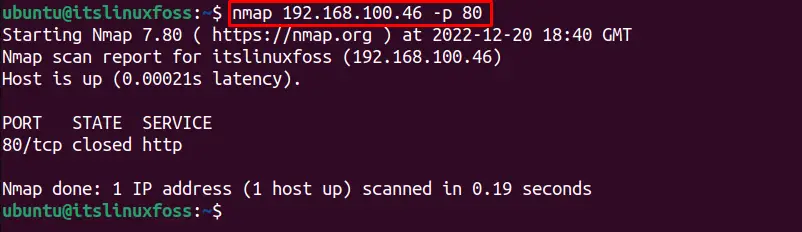
It shows that the target IP address is closed at port 80.
Ping Scanning for Live Host
The Nmap tool is used for scanning the live hosts also. For instance, to scan the host “www.google.com” using the Nmap utility, execute this command:
$ nmap www.google.com
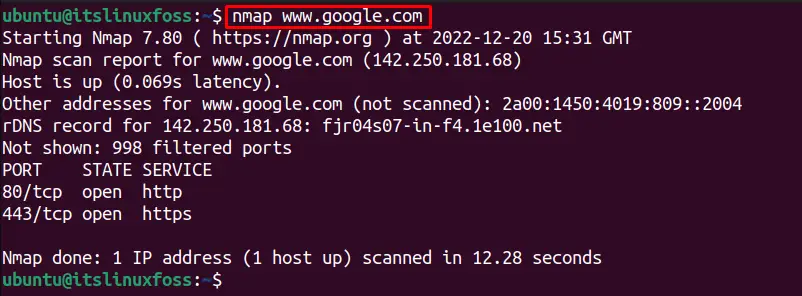
It shows the following details about the host “google”:
- Summary of the Nmap version it scanned and the date and time zone at which the scan was done.
- Provides the IP address of the remote server Google.
- Provides the iPv6 address.
- Filtered ports (Which were not specified by Nmap whether open ports or closed ports)
- Provides details about the Port (port number, protocol), State, and Service of the port.
IP Address Scanning
The main purpose of the Nmap utility is to scan the ip addresses to discover the available hosts on the network. If you want to know what devices are on my network or to ping scan for a specific target, the “sn” and “sP” options are available. Both options scan the network, while the “sn” is
a replacement for the “sP” flag.
To scan a single host using the Nmap tool to check if it is online, use the following command:
$ nmap -sn 192.168.100.46
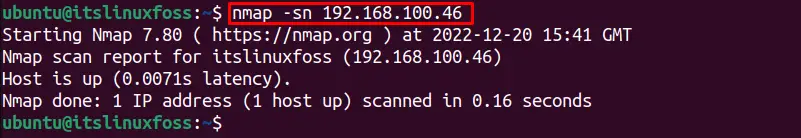
It shows that the targeted IP address is connected.
We can also specify the subnet for discovering the host using the Nmap as given below:
$ nmap -sn 192.168.100.46/24
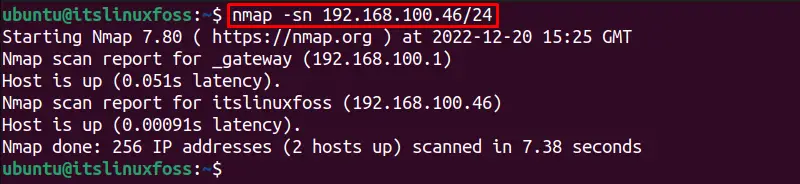
We can scan a range(1 – 255) of IP addresses to discover which hosts are online:
Note: The range 1 -255 shows all the users available at that IP address.
$ nmap -sn 192.168.100.1-255
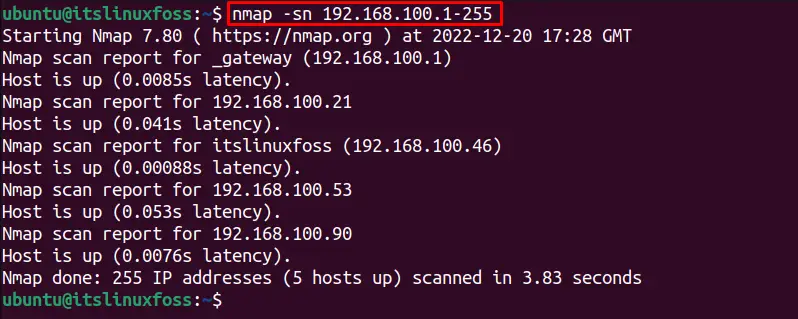
It shows that 5 hosts are connected to the network.
Similarly, another method to check all the online hosts, the below-mentioned command is used:
$ nmap -sn 192.168.100.*
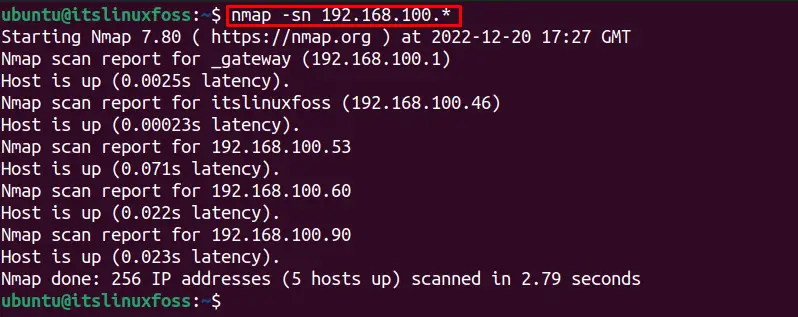
To check for all the IP addresses to discover the online host by excluding specific hosts, use the below command:
$ nmap -sn 192.168.100.* --exclude 192.168.100.46
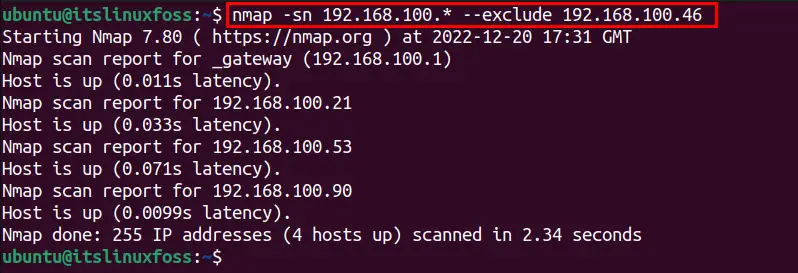
We can simply exclude a range of IP addresses from the scan to get the online hosts on the network, using the below command:
$ nmap -sn 192.168.100.* --exclude 192.168.100.1-50
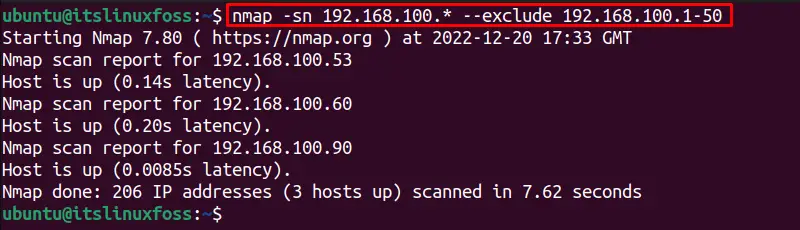
Similarly, the “sP” flag is used to scan the IP address as done previously with the “sn” option.
To scan for a particular IP address host if it is online, using the “sP” option use the following command:
$ nmap -sP 192.168.100.46
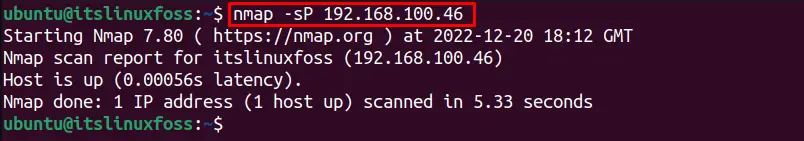
It shows 1 host is alive.
To check all the connected hosts on a network with the range (1 – 255), this command is utilized:
$ nmap -sP 192.168.100.1-255
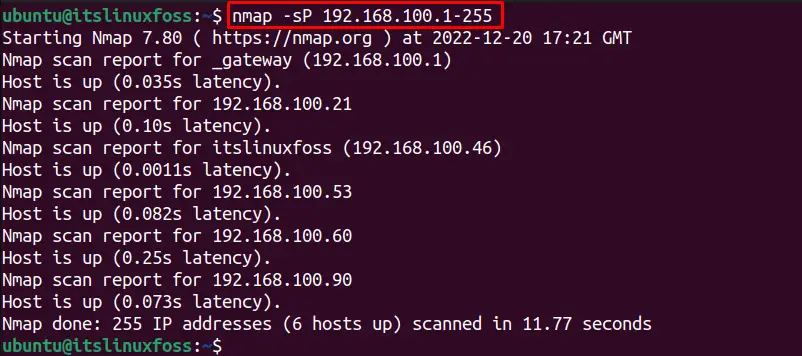
Another method to check all the connections on a network using the “sP” flag, the below-written command is executed:
$ nmap -sP 192.168.100.*
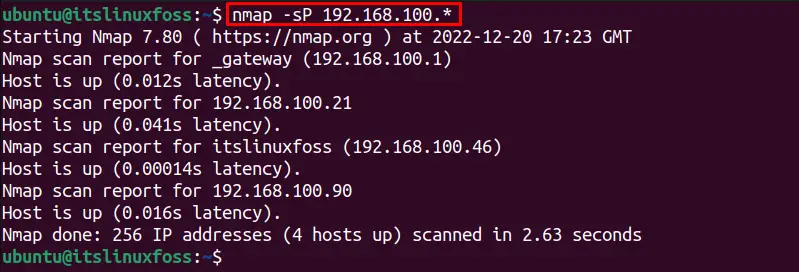
The “script” option allows the users to automate the scanning tasks using the built-in utility NSE (Nmap Scripting Engine) that uses the broadcast-ping. The scripts send the raw data packets to ping sweep, which requires sudo privileges. This option is very helpful for getting additional information about the online hosts on the network which provides all the host’s details including the mac address.
The following command is utilized to discover the hosts using the broadcast-ping script on a network given below:
$ sudo nmap --script broadcast-ping 192.168.100.*
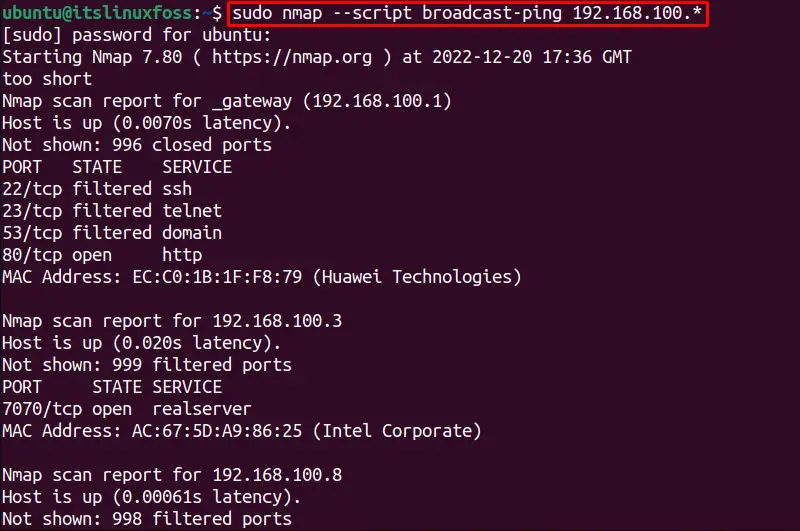
It will consume a few seconds to show all the details about the connected hosts:
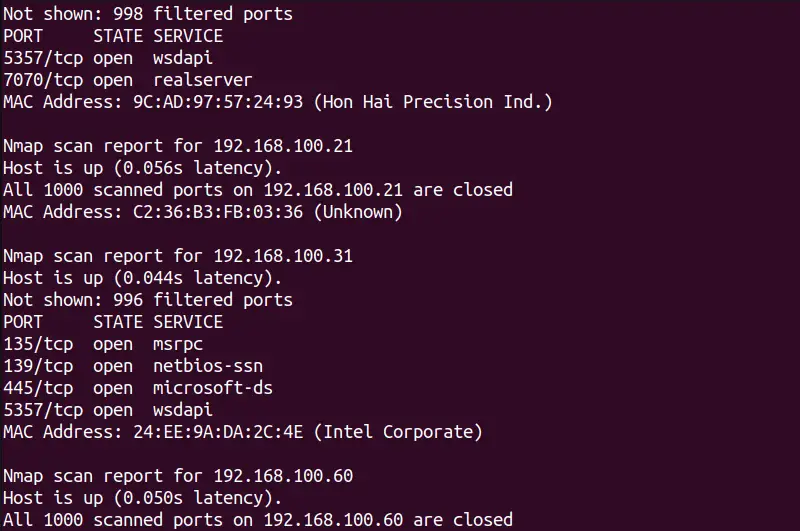
The output shows additional details about all the hosts alive on a network.
The “resolve-all” option in Nmap ping sweep is used to send a ping request to all hosts with duplicate or the same domain name instead of the first domain name. For instance, to scan for an IP address and show the hostname in the output if it can be resolved:
$ nmap -sP --resolve-all 192.168.100.46
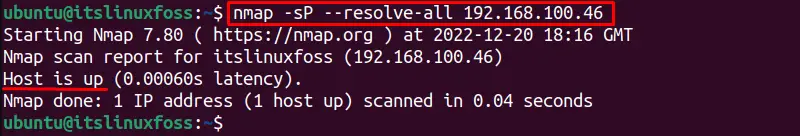
If an IP address is not alive it will try to resolve the network connection and shows the status if it has resolved or not:
$ nmap -sP --resolve-all 192.168.100.35
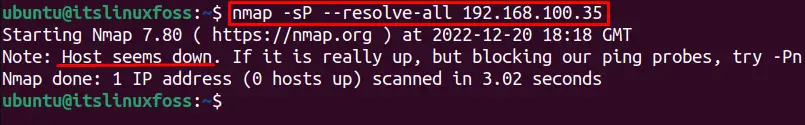
The specified IP address is not alive.
Similarly, we can specify the maximum resolution time for several IP addresses using the “max-RTT-timeout” option of the Nmap tool. It will take a maximum scan time which will be specified with this option.
For instance, the below command will take a maximum of 100ms to scan all the online hosts within a network:
$ nmap -sP --max-rtt-timeout 100ms 192.168.100.*
If you want the Nmap tool to wait for a specific time for an IP address you can specify the “min-RTT-timeout” time with it. For instance, the below command will wait for the “192.168.100.46” IP address for 50ms, if the host is connected before the minimum time it will show the output else if the host is offline it will wait for a minimum specified time:
$ nmap -sP --min-rtt-timeout 50ms 192.168.100.46
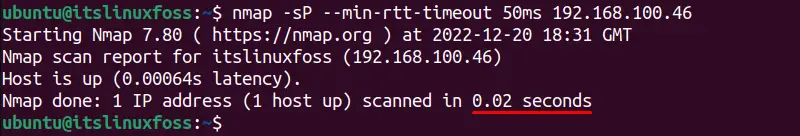
The host is alive and it did not wait for a minimum specified time.
This is all about the nmap ping sweep in Linux.
Conclusion
The Nmap tool is easily used for the ping sweep for discovering the online hosts within a network. The Nmap ping sweep can be used to scan for the specific communication protocol, port number, live hosts, IP address, or range of IP addresses. Moreover, the subnet IP addresses can be to scan the connected hosts.
