The SSH port forwarding in Linux is the method of tunnel traffic using the SSH connection. In SSH forwarding mode, the SSH client listens on a particular port and forwards the traffic to that port on an SSH server through a secure connection. The SSH port forwarding can be done locally or remotely via the default 22 port used for SSH connections.
This article will guide you through the SSH port forwarding basics and different methods with the following timeline:
- How to Do SSH Port Forwarding on Linux?
- SSH Port Forwarding on Local Machine
- Dynamic SSH Port Forwarding
- SSH Port Forwarding on Remote Machine (Reverse Port Forwarding)
Let’s start with the basic knowledge of SSH port forwarding in Linux.
How to Do SSH Port Forwarding on Linux?
The SSH port forwarding can be from a local to a remote server, from a remote to a local server (Reverse), or on a dynamic server. This section will explain SSH forwarding on the local machine, remote machine, and dynamic port forwarding.
Note: We can simply use the command to connect via the SSH server.
ssh <user-name>@<ip-address> -p <port-number>
Replace the username with the remote username, ip-address with the remote server IP address, and the port number with the port on which you want to establish the SSH connection, or use port 22” for the default SSH port.
SSH Port Forwarding on Local Machine
To connect via the SSH server, we can simply use the “ssh <user-name>@<ip-address> -p <port-number>” command. Replace the username with the remote username, ip-address with the remote server IP address, and the port number with the port on which you want to establish the SSH connection, or use port 22” for the default SSH port.
$ ssh [email protected]
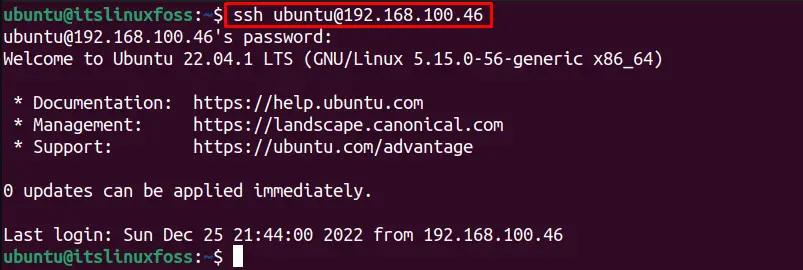
The SSH connection is established.
The “L” option with the SSH is used for SSH port forwarding. The general syntax for SSH forwarding is shown below:
$ ssh -L <local-port-numner>:<remote-ip-address>:<remote-port-number> <remote-user-name>@<remote-ip-address>
The port forwarding command details are as follows:
- L: Allows the SSH port forwarding.
- local-port-number: Change it with the desired local port number you want to tunnel.
- remote-ip-address: Change it with the remote server IP address.
- remote-port-number: Replace it with the desired remote server port which wants to receive the SSH traffic.
- remote-user-name: Replace with the username of the remote server.
For instance, if we want to tunnel the SSH port number “3000” traffic to the IP address 192.168.100.46 on its port number “40000”, the below command is utilized:
$ ssh -L 3000:192.168.100.46:4000 [email protected]
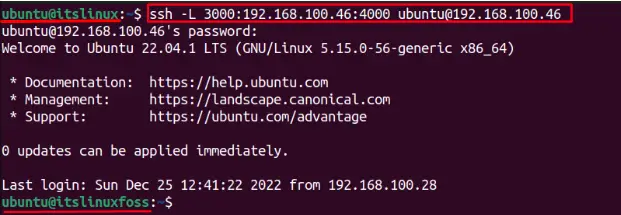
The local machine has no access to the remote server. If you look closely, the hostname is also changed from “itslinux” to the remote user hostname “itslinuxfoss”, which verifies that the local machine now has access to the local server and forwards the traffic on port “4000”.
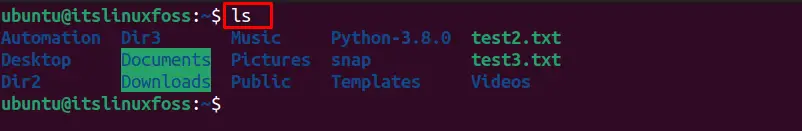
To run the “ls” command on the remote server with SSH port forwarding, that prints the list of directories for the remote machine:
$ ls
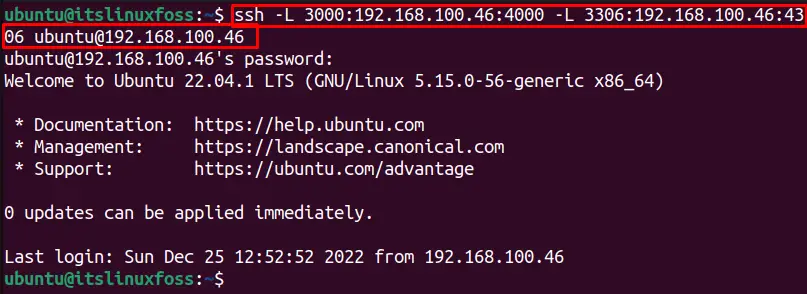
Similarly, multiple ports can be forwarded simultaneously to a remote server using the below single command:
$ ssh -L 3000:192.168.100.46:4000 -L 3306:192.168.100.46:4306 [email protected]
Let’s run another command ”pwd” on the remote server with SSH port forwarding that shows the current working directory for the remote server:
$ pwd

It shows the current working directory of the remote user.
If you want to create a tunnel to the remote server but don’t want to execute the commands remotely from the other machine, the “N” option can be utilized. For instance, to forward the traffic of port “3000” to the remote server port “4000” without allowing the remote user to run the commands on the local machine, follow the below command:
$ ssh -N <local-port-numner>:<remote-ip-address>:<remote-port-number> -L<remote-user-name>@<remote-ip-address>
$ ssh -N [email protected] -L 3000:192.168.100.46:4000
Similarly, If you want to keep running the tunnel to the remote server in the background, use the “f” flag. The “f” flag allows the users to keep SSH port forwarding in the background. It performs other functions in the foreground, whose syntax is as follows:
$ ssh -f <local-port-numner>:<remote-ip-address>:<remote-port-number> -L <remote-user-name>@<remote-ip-address>
$ ssh -f 3000:192.168.100.46:4000 -L [email protected]
Dynamic SSH Port Forwarding
The local and remote SSH port forwarding allows the tunneling on specific ports while the dynamic port forwarding allows a full range of the TCP transmission across a range of ports. The dynamic port forwarding treats your machine as the SOCK proxy server, which listens on the default port “1080”.
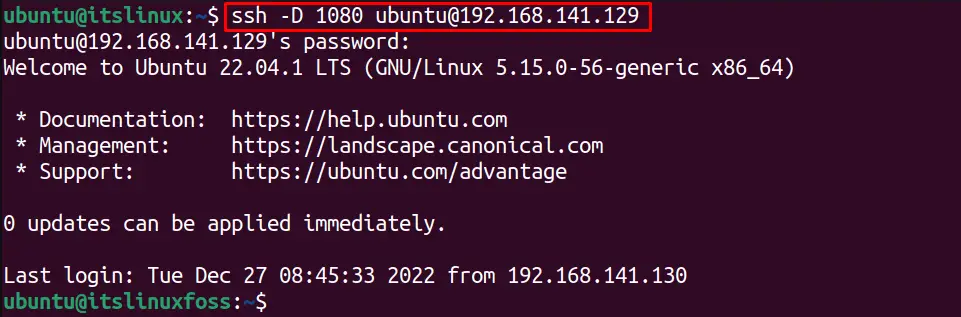
The “D” option provides dynamic port forwarding. For instance, to create the SSH port forwarding on port “1080”, execute the below command:
$ ssh -D 1080 <remote-user-name>@<remote-ip-address>
For instance, the below command will use as the SOCKS proxy on 1080 port number that will connect to the remote server having ip address “192.168.100.46”:
$ ssh -D 1080 [email protected]
SSH Port Forwarding on Remote Machine (Reverse Port Forwarding)
The SSH port forwarding can be done on the remote server from the local server using the “R” option. It also reverses the SSH port forwarding as the remote data is accessed from the local machine. The general syntax of the remote port forwarding as written below:
$ ssh <reote-user-name>@<remote-ip-address> -R <local-port>:<local-ip-address>:<remote-port>
For example, to forward the traffic of the remote server on port “4000” to the local server “3000”, the following command is used:
$ ssh [email protected] -R 3000:192.168.141.130:4000
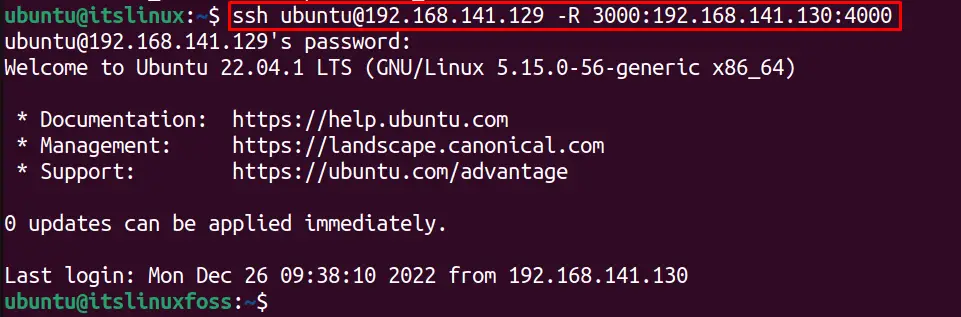
The remote server traffic is tunneled through port “4000” to the local server on port “3000”. The output shows that the terminal hostname is changed from the “itslinux” local server name to the “itslinuxfoss” remote server. The remote server traffic is forwarded to the local server.
Let’s check the “hostname” of the remote machine from the local machine by executing the following command:
$ hostname

The remote user hostname is “itslinuxfoss”.
Alternatively, we can use the below steps to forward the traffic of a remote server port.
Open the “SSH config” file in the nano editor:
$ sudo nano /etc/ssh/sshd_config
Navigate to the “# GatewayPorts no” and remove the “#” symbol to make the GatewayPorts yes as shown below:
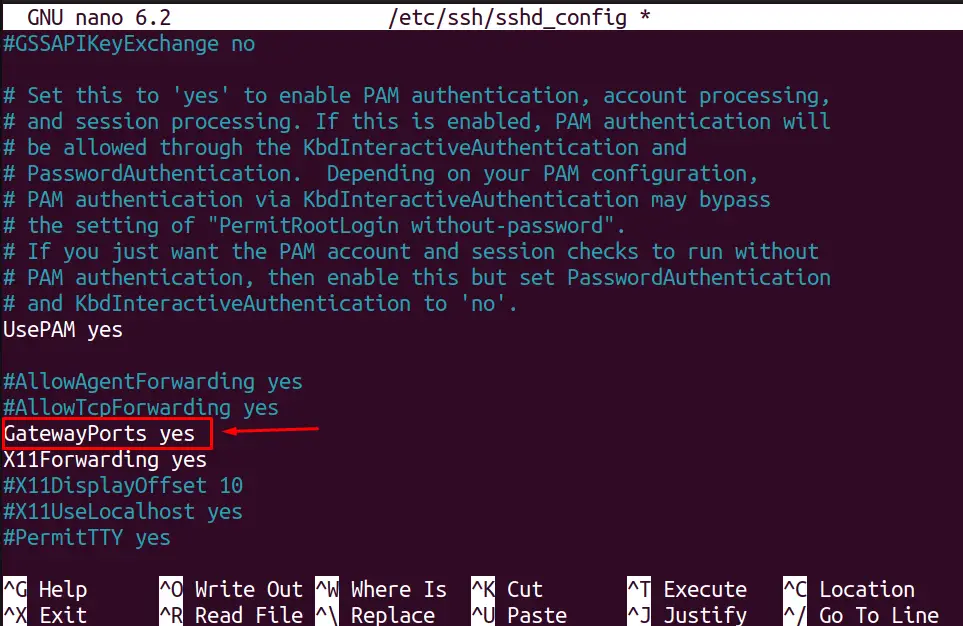
Press Ctrl + O to save the changes in the file and then use the “Ctrl + X” shortcut keys to quit the editor.
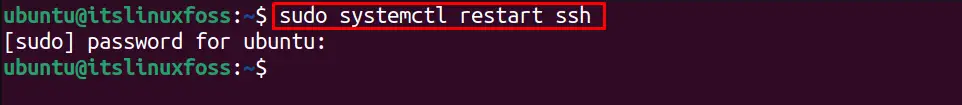
Restart the SSH service with the below systemctl command:
$ sudo systemctl restart ssh
Now, we can perform the port forwarding in Linux on the remote server by using the below command:
$ ssh [email protected] -R 3000:192.168.141.130:4000
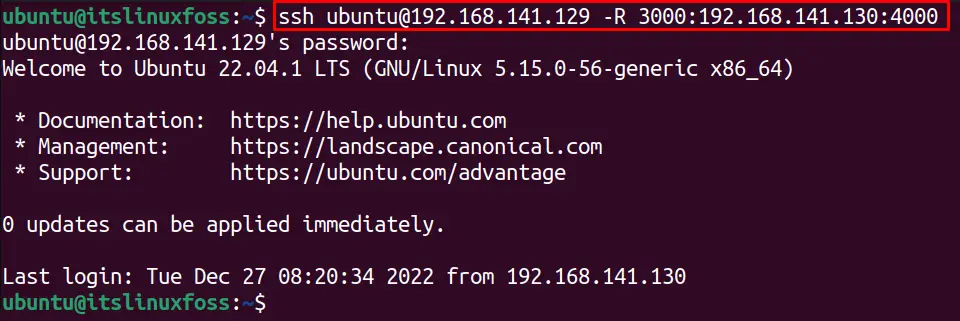
The remote port “4000” is forwarding traffic on the local port “3000” via the SSH.
That’s how you can perform SSH port forwarding on Linux.
Conclusion
The SSH port forwarding on Linux allows to forward the traffic of the remote server to the local server on a specific port or vice versa. This will allow the users to access other server resources by bypassing the network restrictions. The SSH port forwarding in Linux is done using the “L” option with the SSH command. We can perform SSH port forwarding with different options to control the other system resources.
Moreover, we forward the remote server traffic to the local server using the “R” option, which is also called reverse or remote port forwarding.
