In Linux, the “telnet” is the command line tool used for checking the open ports and also for the connection to the remote over the TCP/IP networks. But there are various alternative tools that can be considered for checking the open ports such as “nmap”, “netstat”, “netcat”, “/dev/tcp”, or “lsof”.
This post will demonstrate the alternatives for checking the open ports besides telnet in Linux.
- Using nmap
- Using netstat
- Using lsof
- Using netcat (nc) | For Specific Port
- Using /dev/tcp | For Specific Port
Using nmap
The “namp” is the networking tool that is utilized for scanning the network connection and searching for the open ports in the network. To install it, run any of the below commands based upon your Linux distro:
$ sudo apt install nmap #For Debian/Ubuntu
$ sudo dnf install nmap #For Fedora
$ sudo yum install nmap #For CentOS/RHEL
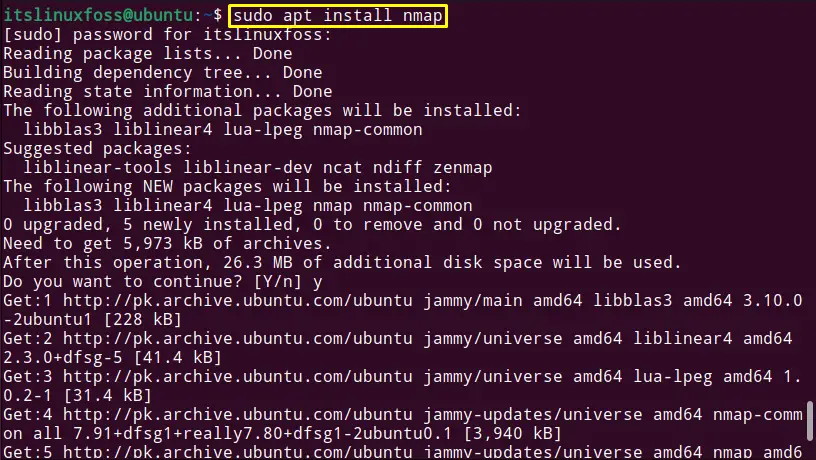
The “nmap” tool is installed.
Run the “nmap” tool with the “F” flag for the fast scan and type the IP address network:
$ sudo nmap -F 192.168.119.129
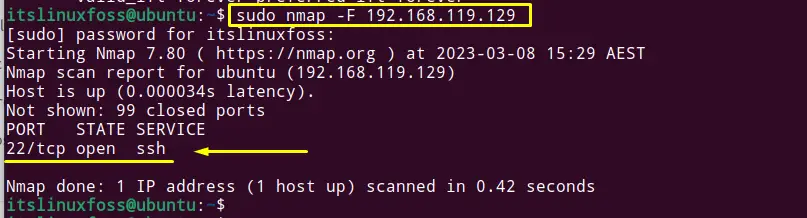
The SSH port 22 is the open port.
Using netstat
The second alternative for checking the open ports is by using the “netstat” command. A command line tool that is considered for retrieving information on connections, interface statistics, and other network-related tasks.
The “netstat” command comes with the installation of “net-tools” packages, run the below-given command to install it:
$ sudo apt install net-tools #Debian/Ubuntu
$ sudo yum install net-tools #CentOS/RHEL/Fedora
$ sudo pacman -S netstat-nat #Arch-Linux
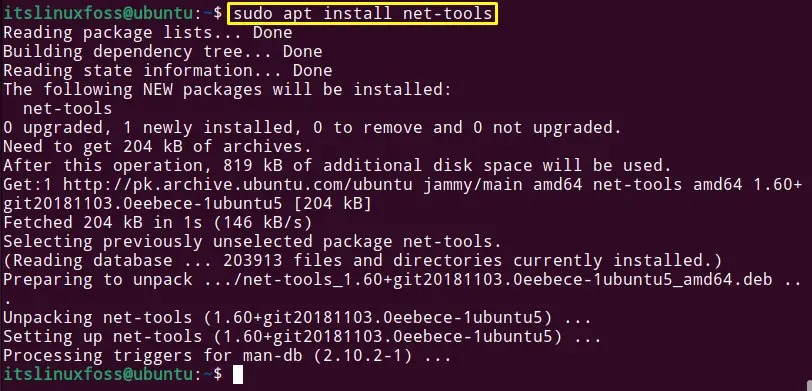
The “net-tools” package is installed.
Run the netstat command in the terminal with the following options:
$ netstat -tuplen
The command’s options are described as
- “t” flag for TCP connections.
- “u” flag for UDP connections
- “P” flag for programs ID/Name for sockets
- “l” flag for listening sockets
- “e” flag for extending information
- “n” flag for displaying dotted IP addresses
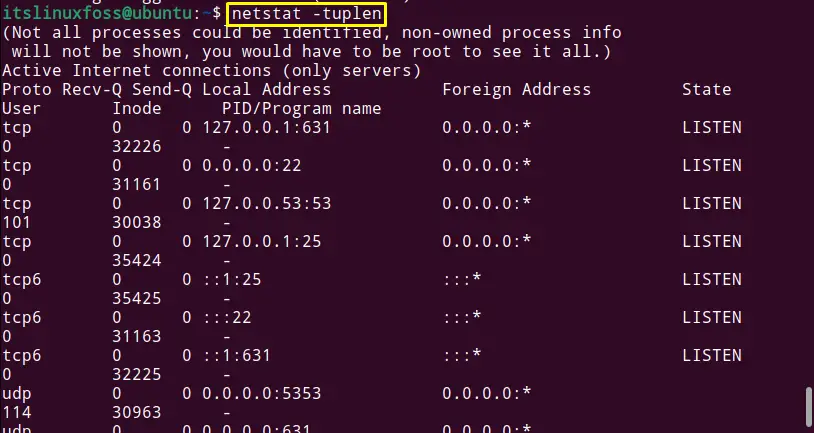
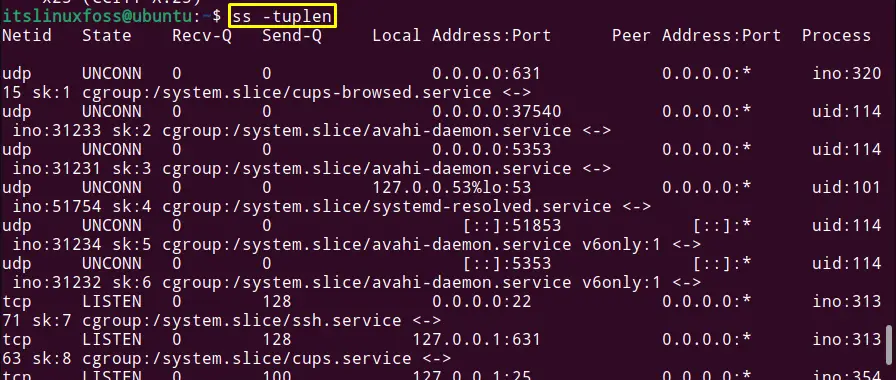
Ports number 631, 22, 53, and 25 are in the open state
Note: The user can also use the “ss” (Replacement of netstat) utility instead of “netstat” to get the same results but with detailed more information:
$ ss -tuplen
Using lsof
The “lsof” is the command line tool used for listing the open files in the Linux operating system. It can be used for displaying the processes listening on particular ports. Let’s see how it can be used as an alternative to telnet:
Install lsof on Linux
The “lsof” command’s support may not be available by default (due to minimal/restricted installation). To install it, use the command:
$ sudo apt install lsof #Debian/Ubuntu
$ sudo yum install lsof #RHEL/CentOS/Fedora
$ sudo zypper install lsof #OpenSUSE
$ sudo pacman -S lsof #Arch-Linux
The “lsof” utility is installed.
The following command will display all process listening on the particular ports:
$ sudo lsof -i -P -n | grep LISTEN
The command option is described as
- “i” flag for selecting IPv4 files.
- “P” flag for selecting PIDs (process ID).
- “n” flag for listing no hostnames.
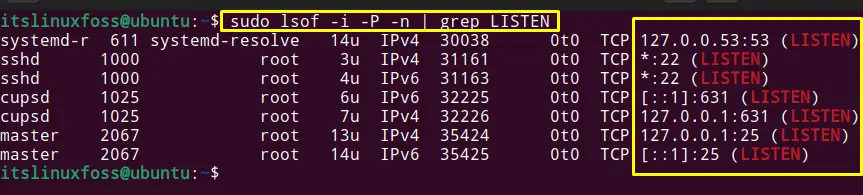
The Listening ports for all the processes are listed.
Using netcat (nc) | For Specific Port
The “nc” (netcat) is the tool considered for scanning ports and transmitting data via UDP and TCP protocols. To install the “nc” command, the following are used:
$ sudo apt install netcat #For Debian/Ubuntu
$ sudo dnf install nc #For Fedora
$ sudo yum install nc #For CentOS/RHEL
The “nc” (netstat) utility is installed.
The syntax for scanning the ports on the network using the “nc” command is given below:
Syntax:
$ nc -zv <IP address> <port number>
The syntax is described as:
- The “nc” command for scanning ports.
- “z” flag for scanning the open ports.
- “v” flag for verbose mode.
- “IP address” of the network to scan.
- “port number” to check the particular port.
To check the port 22 is open or not, the following command is used:
$ nc -zv 192.168.119.129 22
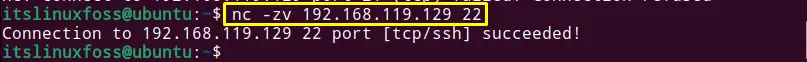
The successful connection with port 22 shows that port 22 is in the open state.
Using /dev/tcp or /dev/udp | For Specific Port
The open ports can also be checked using the /dev/tcp or /dev/udp by entering the host/network and port number to check. Use the following command syntax for scanning the open ports:
Syntax:
$ echo > /dev/tcp/[host/Network IP]/[port] && echo "Port is open"
Or
$ echo > /dev/udp/[host]/[port] && echo "Port is open"
The syntax is described as
- Enter the “host/network IP address” with the “port” number in the echo command.
- “&&” (AND) operator is joined with an echo statement to get the successful execution of the command.
To check the port 22 is open or not, the following command is used based upon the syntax:
$ echo > /dev/tcp/192.168.119.129/22 && echo "Port is open"
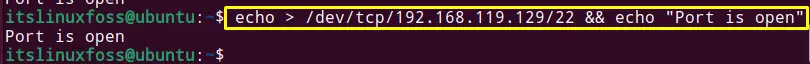
Port 22 is in the open state.
Conclusion
In Linux, the user can use the “nmap”, “netstat”, “netcat”, “/dev/tcp” or “lsof” tools as an alternative to the “telnet” tool. To use the “nmap”, “netstat” and “dev/tcp or /dev/udp”, run it with the network/host IP address and port number to check. To use the “netcat”, run it with “tuplen” flags in the terminal while using the “lsof” run it with the “i”, “P” and “n” flags.
This blog has illustrated the alternatives besides telnet for checking open ports in Linux.
