Reverse SSH tunneling is a technique used to connect to a remote computer over an SSH connection. It securely accesses a remote device, such as a server or database, without opening its external ports. It bypasses firewalls and accesses a system after a firewall or NAT router.
Considering its significance, this guide will illustrate the working of SSH tunneling in a reverse manner.
How Does Reverse SSH Tunneling Work?
First, the connections from the local computer to the remote computer are established using SSH. Then, the local computer forwards any incoming connections on a specific port to the remote computer. It creates an encrypted tunnel between a remote user and the internal system to ensure secure access.
How to Set Up Reverse SSH Tunneling?
To set up reverse SSH tunneling, the remote computer needs to be able to accept incoming connections on a specific port. The step-by-step instructions are provided below:
Prerequisite: Check the SSH Service Status
It is better to check the status of SSH services before any configuration regarding SSH. To check the services of SSH, utilize the “systemctl” command with the “status” option as below:
$ sudo systemctl status ssh
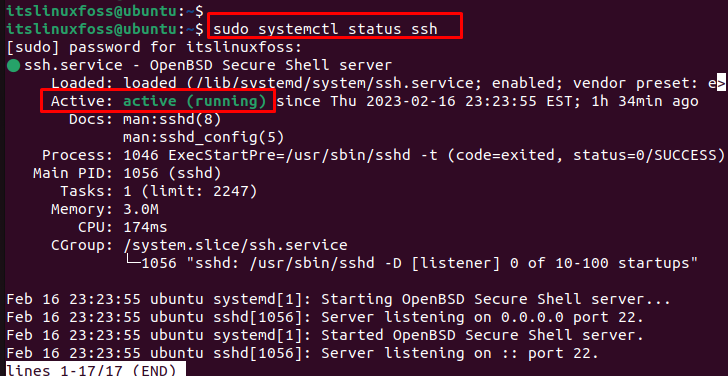
The output shows that ssh services are in an active state.
Note: If the ssh services are dead, follow the link to configure the SSH.
Set Up Reverse SSH Tunneling
To establish a reverse SSH tunnel, execute the “ssh” command on the local computer. It creates a tunnel between the local and the remote machines. The command syntax is as below:
Basic Syntax
$ ssh -R <remote port>:localhost:<local port> <username>@<remote host>
The description of the above syntax is provided below:
- remote port: port on the remote computer that accepts the incoming connection.
- local port: port on the local computer that will send the connection.
- username: specify the user’s name on the remote computer who will accept the connection.
- remote host: refers to the hostname of the remote machine.
Example:
An example is considered to perform reverse SSH tunneling using the “ssh” command. In this command, specify the “22” as a remote port and “44” as a local host. The username is “roger”, and “ubuntu” identifies the remote host:
$ ssh -R 22:localhost:44 roger@ubuntu
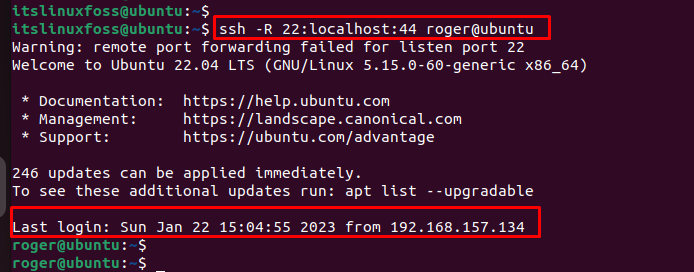
The output confirms that a reverse SSH tunneling connection has been established.
Verify: Reverse SSH Tunneling Connection
To verify the working of the SSH tunnel, execute the “ssh” command by specifying the remote port number, username, and hostname. In our case, “port 22” is utilized by mentioning “roger” as username and “ubuntu” as hostname:
$ ssh -p 22 roger@ubuntu
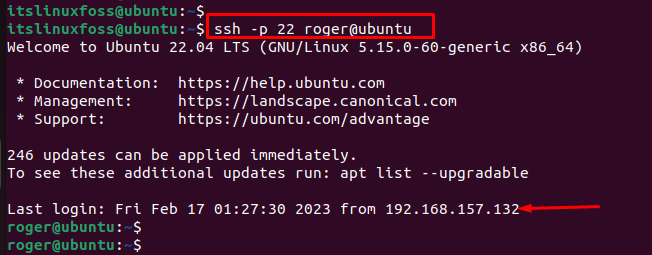
The output verifies that a secure tunnel has been created between the two systems.
Conclusion
Reverse SSH tunneling allows users to access remote systems behind a firewall. To reverse SSH tunneling, execute the “ssh -R <remote port>:localhost:<local port> <username>@<remote host>” command. It offers a secure way to access internal resources like databases, web servers, and other services.
This article has illustrated the step-by-step procedure to reverse SSH tunneling in Linux.
