The OpenSSL s_client is important for analyzing client-side communications. The s_client is useful for testing the client-server to troubleshoot the remote host by using the SSL and TLS connections. The OpenSSL command tests the connections, SSL certificates, and diagnostic reports about the client-side connections.
This guide will emphasize the uses of the OpenSSL s_client command with the help of these topics:
- How to Use the OpenSSL S_Client?
- Test Connections
- Connect Multiple Hostnames
- Disable TLSv1.3 Version
- Debug SSL Connections
- Print SSL Certificates
- Check SSL Certificate Validation
- Check SSL Certificates Expiry Dates
- Verify SSL Connection
- Check SSL Certificate Fingerprint
- Specify the Cipher
- Use Specific SSL Version for Ciphers
- Send Protocol-Wise Message
Let’s discuss the OpenSSL s_client usages.
How to Use the OpenSSL S_Client?
The OpenSSL tool provides several useful options that can be used for a specific purpose. This section will explain the common uses of the OpenSSL S_Client with its options in Linux.
Let’s first check the general syntax for OpenSSL s_client command:
$ openssl s_client -connect <hostname> : <port>
The listed options are described below:
- connect: It checks the connection for the client side and shows the connection details.
- hostname: Replace it with client hostname.
- port: Replace it with the desired port on which the connection will be established.
Let’s get into the practical usage of the OpenSSL_S client.
Use OpenSSL S_Client to Test Connection
The “connect” option is used to test the HTPPS service connection. The server diagnostic report and server certificate information can be found by using the following command:
Note: Port 443 is the default port for HHTP server connection over the SSL/TLS service, and the connectivity is testing for “google.com”.
$ openssl s_client -connect google.com:443
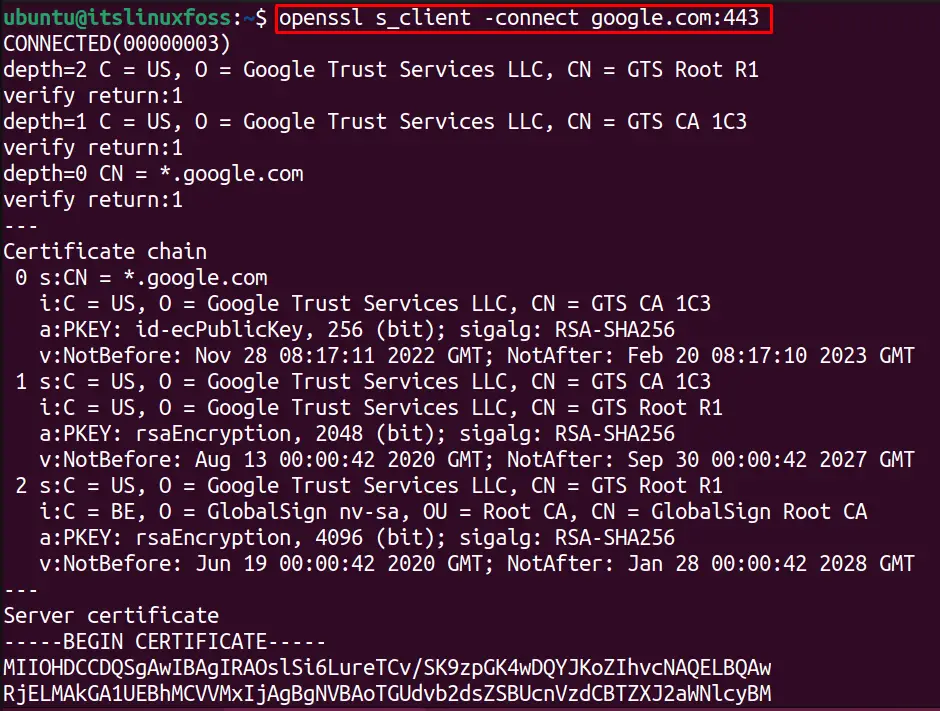
The output shows the connectivity with “google.com”.
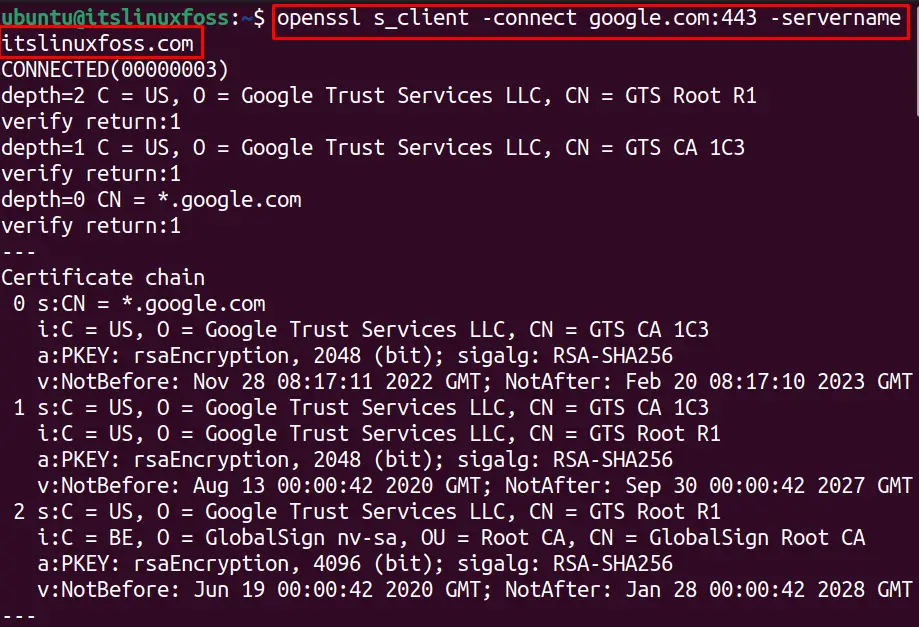
Use OpenSSL S_Client to Connect Multiple Hostnames
Similarly; we can use the OpenSSL S_client to connect to multiple servers using the “-servername” option. For example, the below command will test the connections for “google.com” and “itslinuxfoss.com” with a single command:
$ openssl s_client -connect google.com:443 -servername itslinuxfoss.com
Use OpenSSL S_Client to Disable TLSv1.3 Version
We can test the connection for OpenSSL without any specific TSL/SSL flag. Several TSL/SSL protocols are used to connect to servers such as tls1_1, tsl1_2, ssl3etc.
By default, the S_Client treats with SSL/TSL protocols. But we can specify the version for these protocols as well, which are as follows:
- ssl3: SSL version 3
- ssl2: SSL version 2
- tls1: TLS version 1.0
- tls1_3: TLS version 1.3
- tls1_2: TLS version 1.2
The number with the TSL/SSL protocol defines its version.
To test the connection to “google.com” without using the “tls1_3” protocol, execute the below command:
$ openssl s_client -connect google.com:443 -no_tls1_3
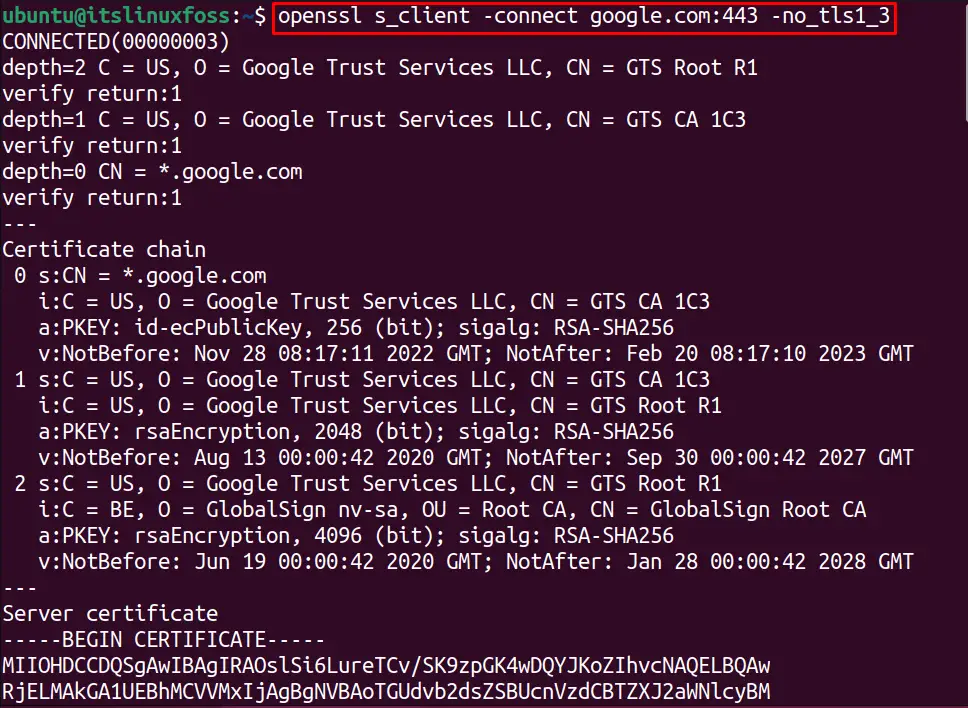
Use OpenSSL S_Client to Debug SSL Connections
We can debug the SSL/TLS connection by using OpenSSL s_client option “-tlsextdebug” is utilized. For example, the below command will debug the OpenSSL connection with “google.com”:
$ openssl s_client -connect google.com:443 -tlsextdebug
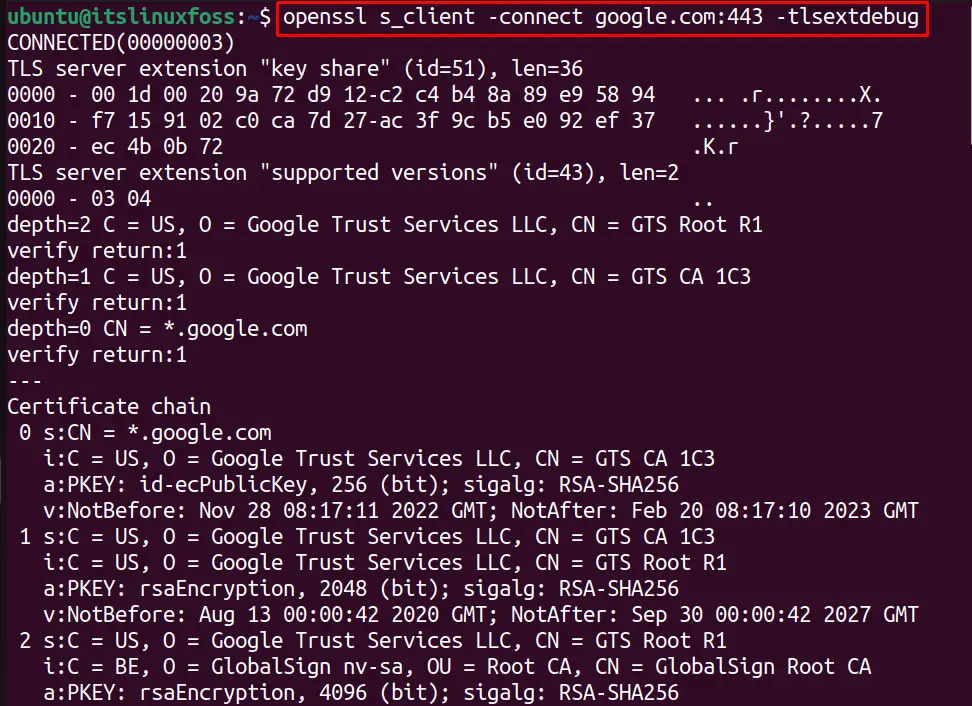
Use OpenSSL S_Client to Print SSL Certificates
The SSL certificates are normally present in a PEM file that contains all the SSL certificate information in a formatted manner. To check the details of the SSL certificates for a server (googel.com), use:
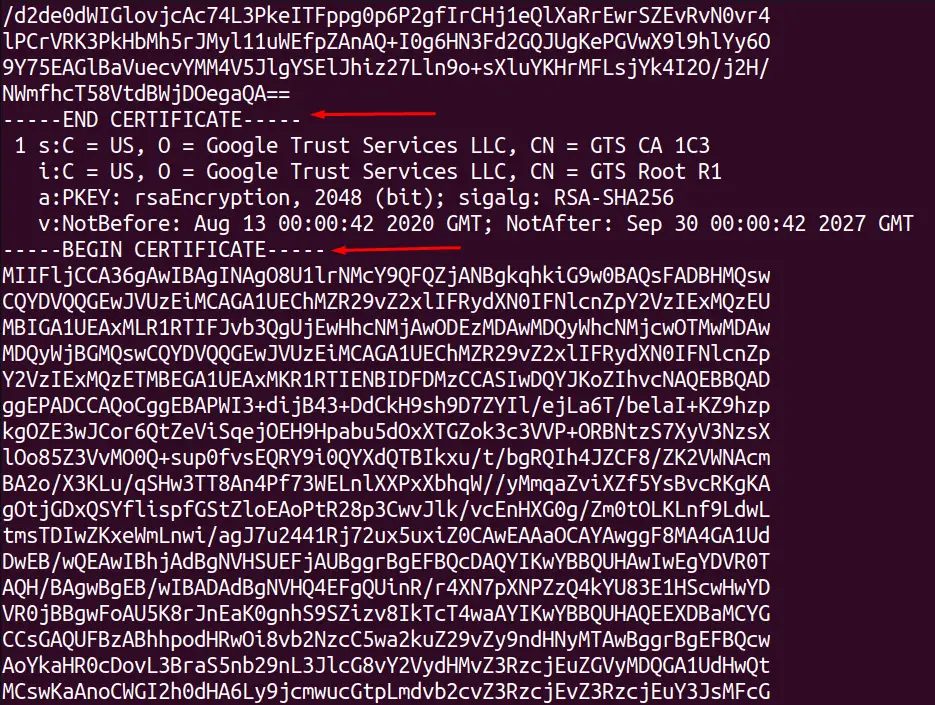
$ openssl s_client -connect google.com:443 -showcerts
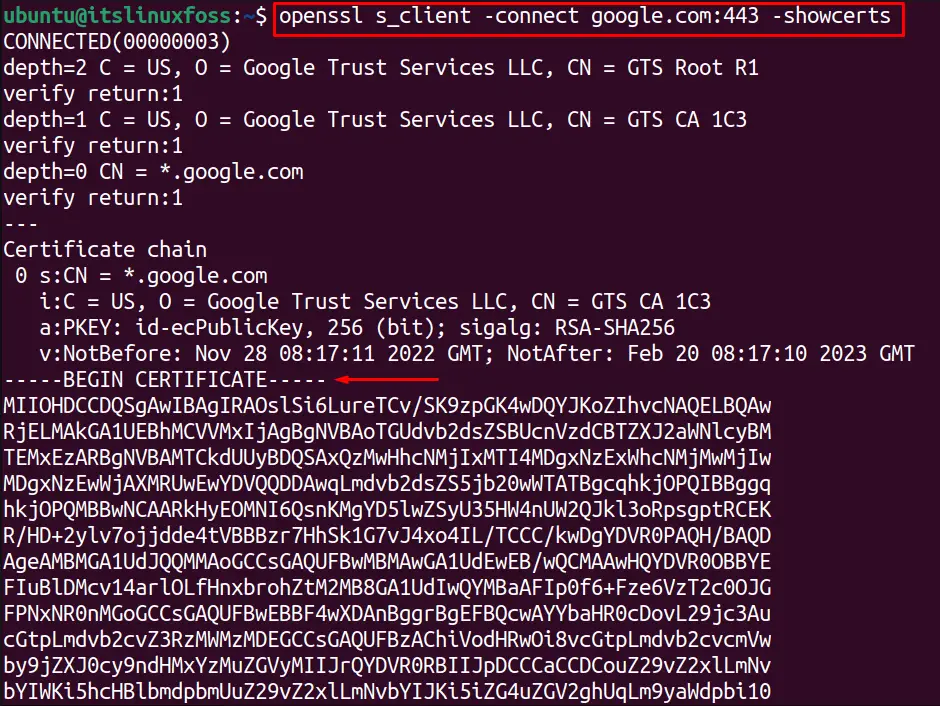
The output shows different SSL certificates details in a specified manner:
Use OpenSSL S_Client to Check SSL Certificate Validation
The SSL certificate validation can be checked by OpenSSL utility using the connect option, and by adding the brief option, we can show fewer details. The below command will tell us the SSL certificates validity:
$ openssl s_client -connect google.com:443 -brief
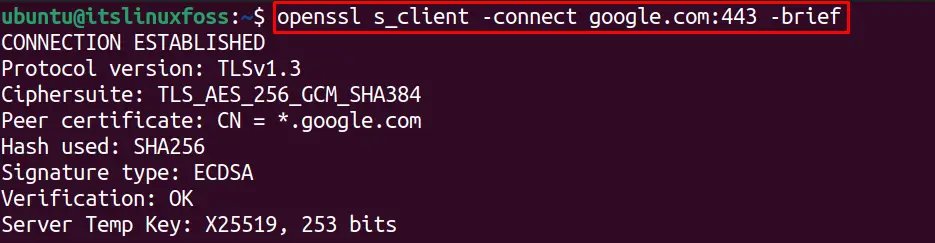
The error-free output shows that the SSL certificates are valid.
Use OpenSSL S_Client to Check SSL Certificates Expiry Dates
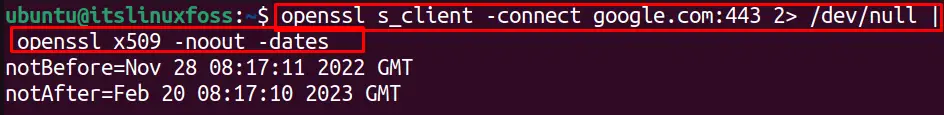
We can check the SSL certificates expiration date for any specific website by using the “dates” option. To display the expiration dates without any encoding, use the “-noout” option. For instance, the below OpenSSL command will display expiry dates for “google.com” SSL certificates:
$ openssl s_client -connect google.com:443 2> /dev/null | openssl x509 -noout -dates
Use OpenSSL S_Client to Verify SSL Connection
The SSL connection to any server can be verified with the “verify_return_error” option. To check the OpenSSL S_Client connection with google.com, run this command:
$ openssl s_client -verify_return_error -connect google.com:443
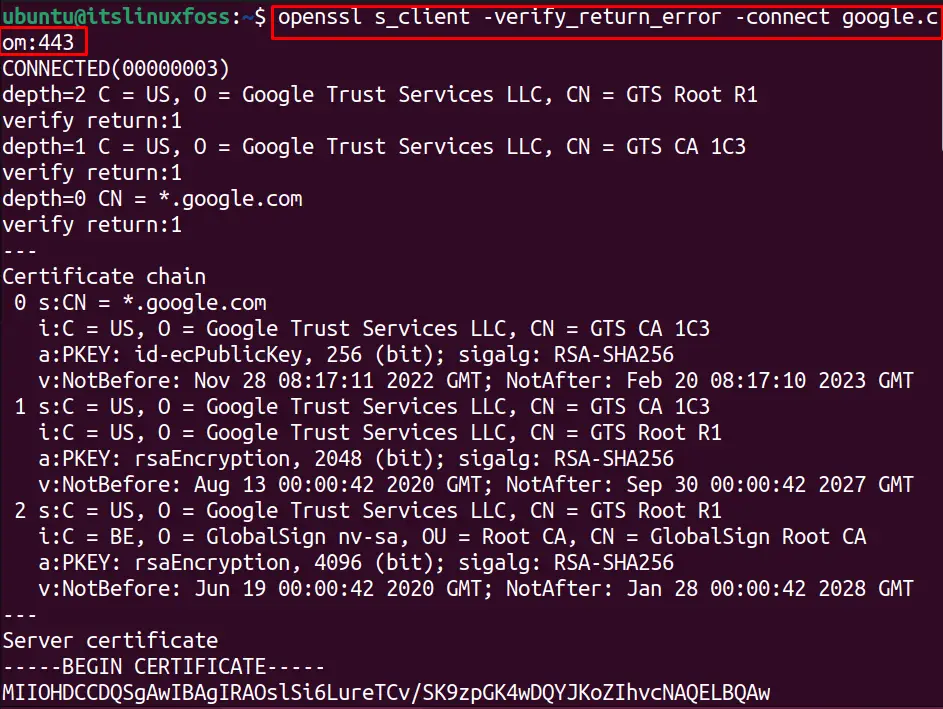
The output shows that the connection is successful and the SSL connection is verified.
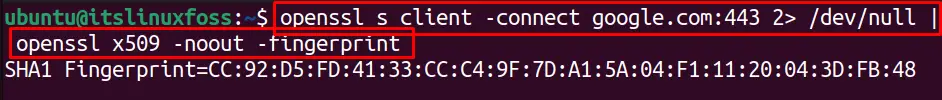
Use OpenSSL S_Client to Check SSL Certificate Fingerprint
Similarly, we can check the SSL certificates fingerprints for google.com by using the “fingerprint” option with the OpenSSL command as shown below:
$ openssl s_client -connect google.com:443 2> /dev/null | openssl x509 -noout -fingerprint
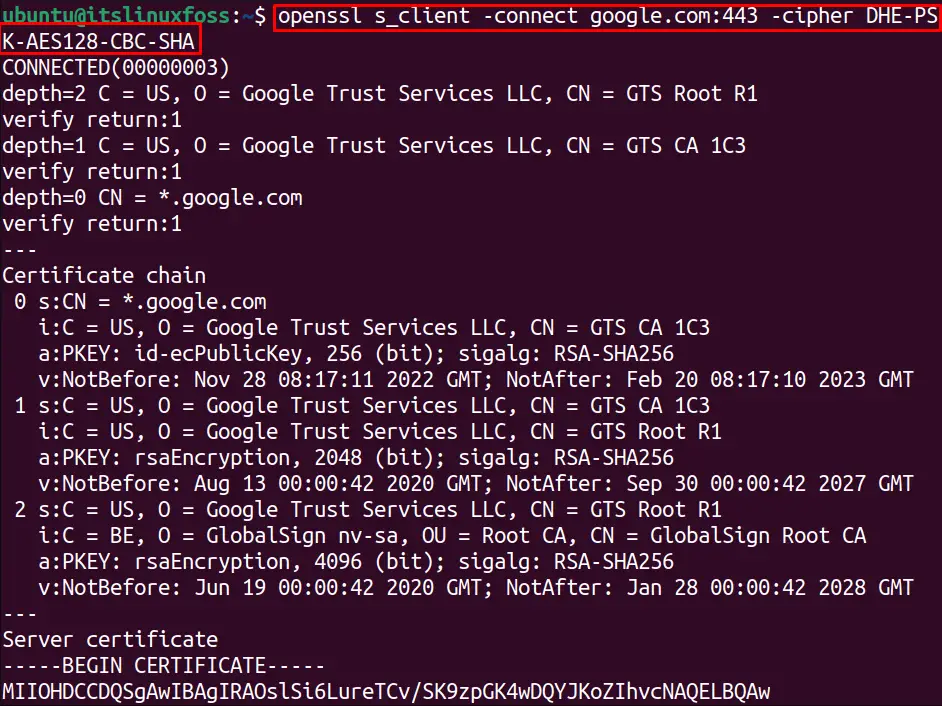
Use OpenSSL S_Client to Specify the Cipher
The encryption type for the SSL certificates can be specified by using the “cipher” option. For example, we have specified a cipher in the below command to connect to a server which will also be specified by the client-server to create a connection:
$ openssl s_client -connect google.com:443 -cipher DHE-PSK-AES128-CBC-SHA
To check all the available OpenSSL ciphers, just write the “ciphers” with the openssl command:
$ openssl ciphers
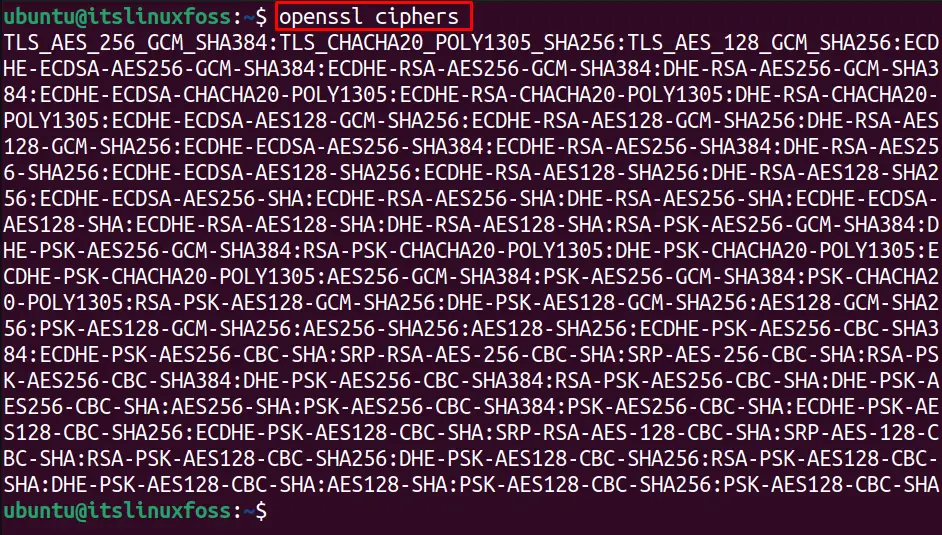
All the OpenSSL ciphers are listed.
Use OpenSSL S_Client to Use Specific SSL Version for Ciphers
In the previous step, we saw a specified cipher was used with the OpenSSL S_client connection. Similarly, we can specify the version of the cipher.
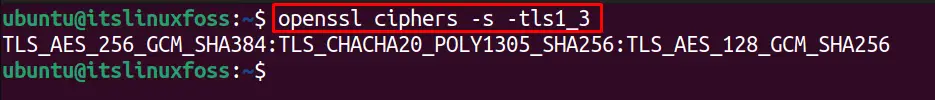
For instance, the below command-line utility uses the “tls1_3” version to list the supported ciphers:
$ openssl ciphers -s -tls1_3
Let’s connect to “google.com” with the “tls1_3” cipher version with the below-written command:
$ openssl s_client -connect google.com:443 -tls1_3
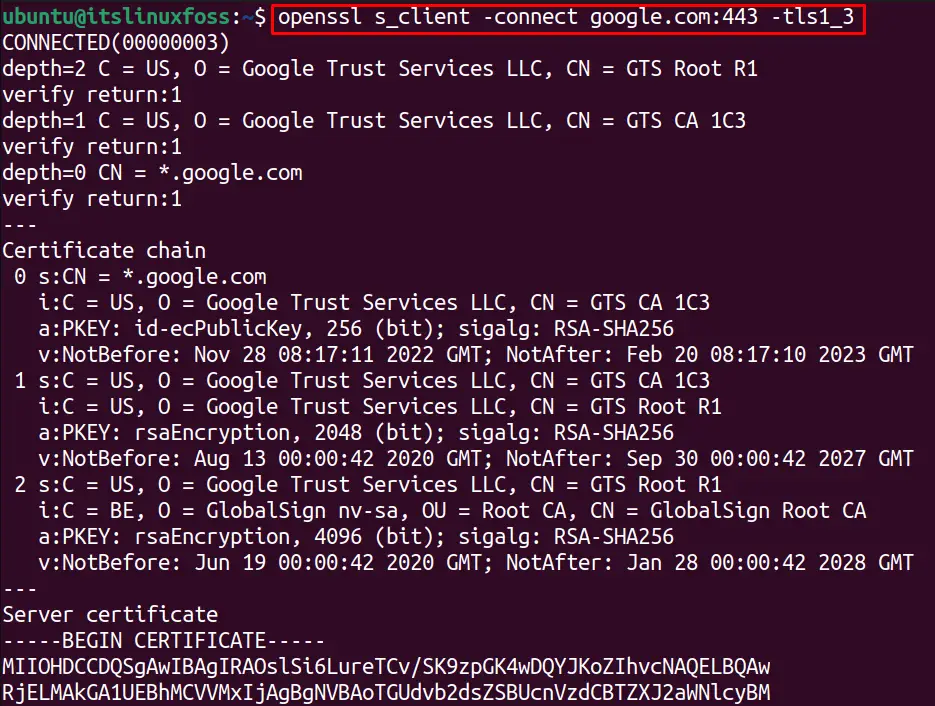
The connection is successfully established with the valid cipher version.
Use OpenSSL S_Client to Send Protocol-Wise Message
Different protocols are supported by OpenSSL, including FTP, IMAP, and SMTP. To text the connection with a specific protocol, the “starttls” option. For example, to test the FTP protocol connection with the google.com, we can utilize the below command:
$ openssl s_client -connect google.com:443 -starttls ftp -servername google.com
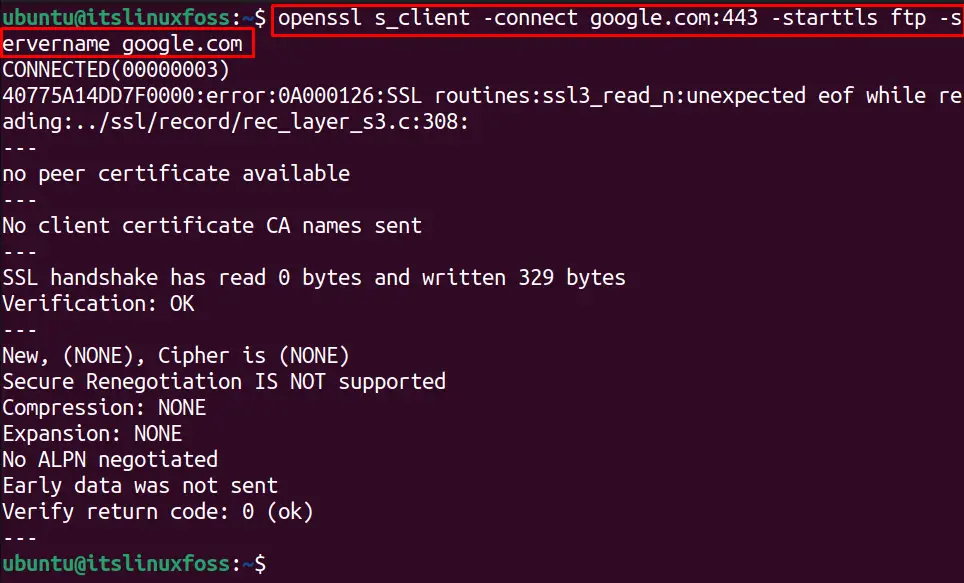
The system is successfully connected with the FTP protocol.
That’s how you can use the OpenSSL_S client in Linux.
Conclusion
The OpenSSL command tests the server connections by using the specified options. This write-up explains the important options commonly used for OpenSSL S_Client connections. The OpenSSL S_Client creates a secure connection with the remote servers explained in this guide.
