SSH is the service by which other Linux machines can be accessed from the terminal, and this method is secure as it is encrypted. The SSH offers secure authentication of the connections to transfer the files/data in an encrypted manner. However, a user can make it more secure by taking additional steps at the system end.
This post will list the possible steps to secure the SSH server in Ubuntu 22.04.
How to Secure the SSH Server in Ubuntu 22.04?
Follow the step-by-step guide to make SSH more secure by making some changes in the sshd_config file:
Step 1: Create Backup of the sshd_config File
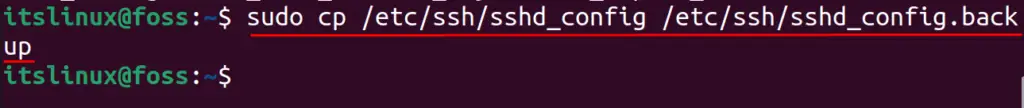
Before making the changes in the configuration file of the SSH server, that is /etc/ssh/sshd_config, make its backup by copying all the contents of the file in a new backup file:
$ sudo cp /etc/ssh/sshd_config /etc/ssh/sshd_config.backup
Step 2: Open the sshd_config File
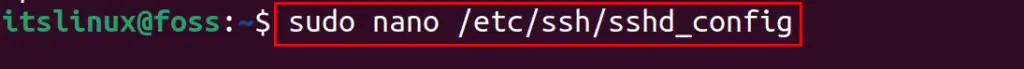
Now, open the configuration file of SSH using the nano text editor:
$ sudo nano /etc/ssh/sshd_config
A file similar to the one mentioned below will be opened on the screen:
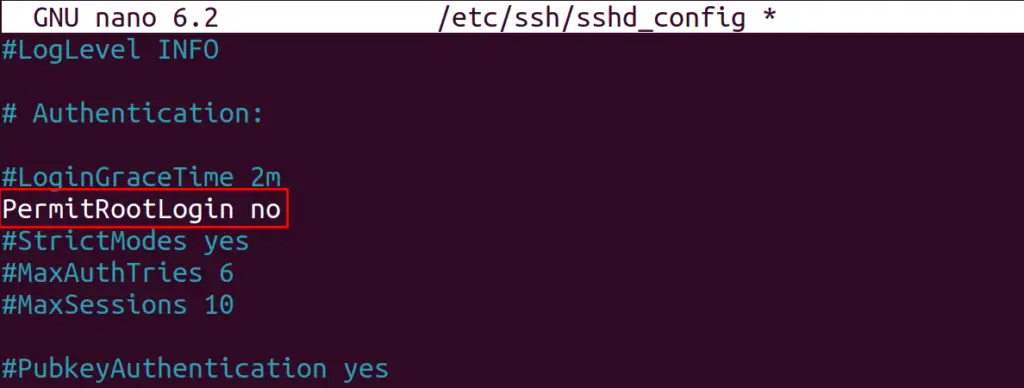
Step 3: Restrict Root Login Access
First, find out the line “#PermitRootLogin” in the file:
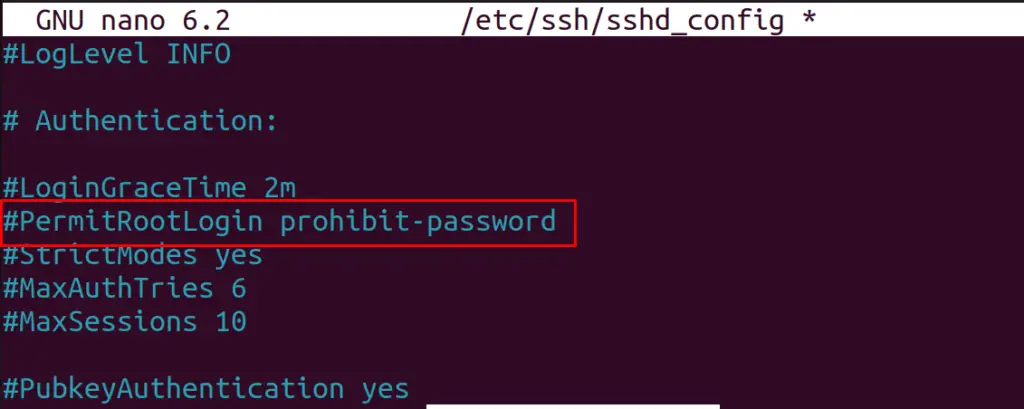
Remove the “#” and replace “prohibit-password” with “no” to deny the root login access:
Step 4: Limit the Access to Specific Users
To limit its access to specific users, type the name of the users who are supposed to use it by typing their name in the “AllowUsers” line:
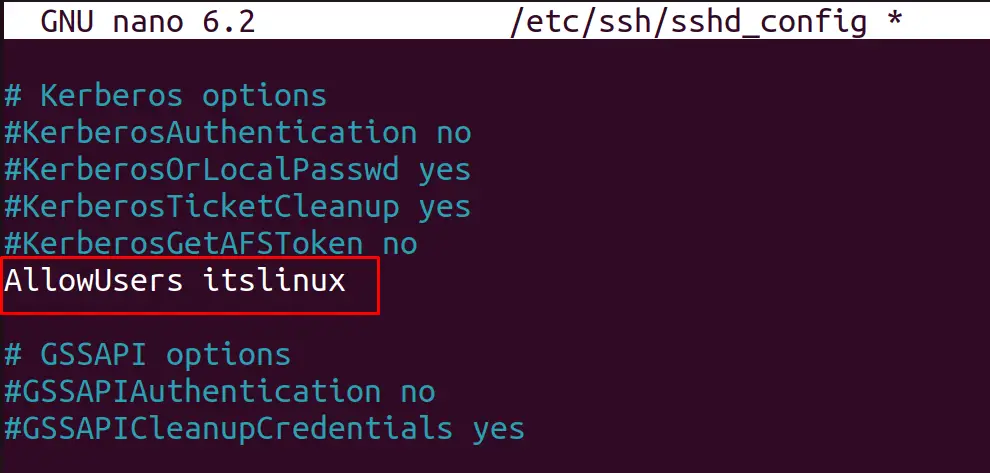
Similarly, using the following syntax, the access to multiple users can be granted:
AllowUsers <user1> <user2>
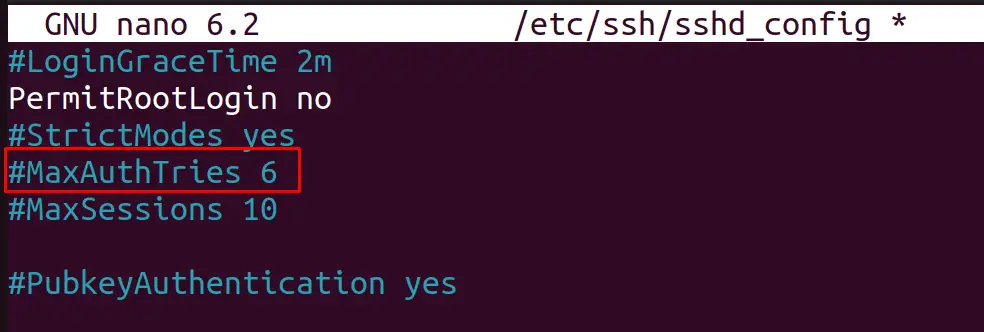
Step 5: Specify the Number of Attempts to Log in
The “MacAuthTries” component in the “sshd_config” file refers to the number of failed attempts that a client can make.
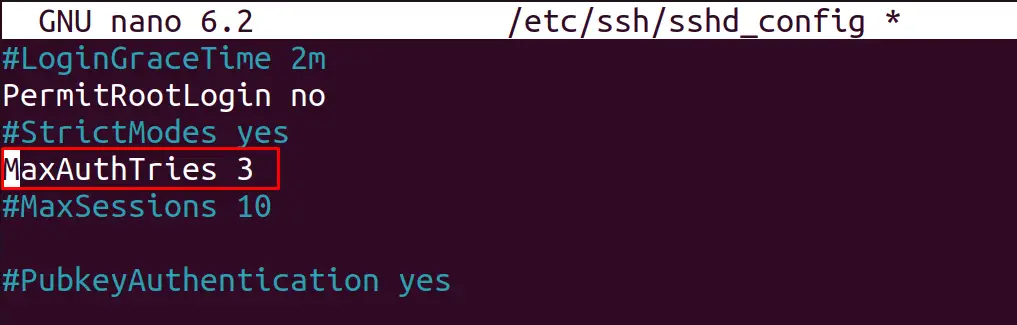
To change it, locate the line, uncomment it and write a new value; in this case, it is set to “3”:
And set it to any number by removing the “#” sign:
Step 6: Disable the Password-Based Authentication
Disable the password-based authentication as we have to add the SSH keys for the authentication which are more secure and protected.
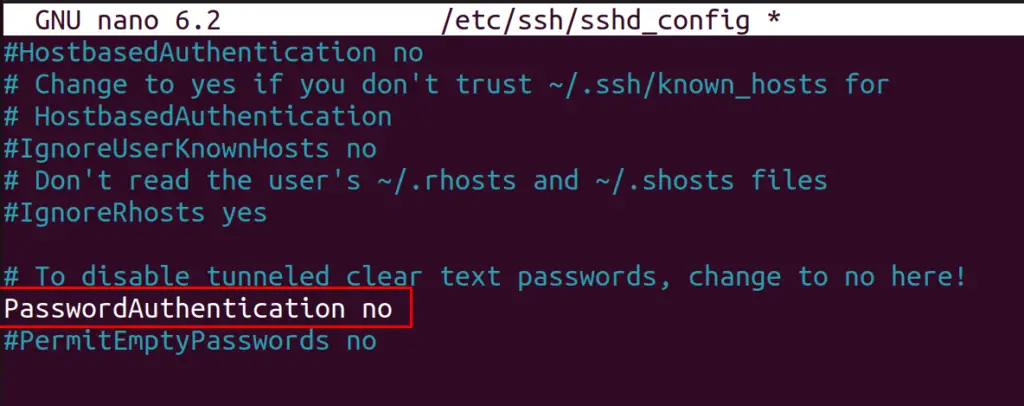
For this, trace the line “PasswordAuthentication”, uncomment it and write “no” as shown below:
Step 7: Do not Accept Empty Password
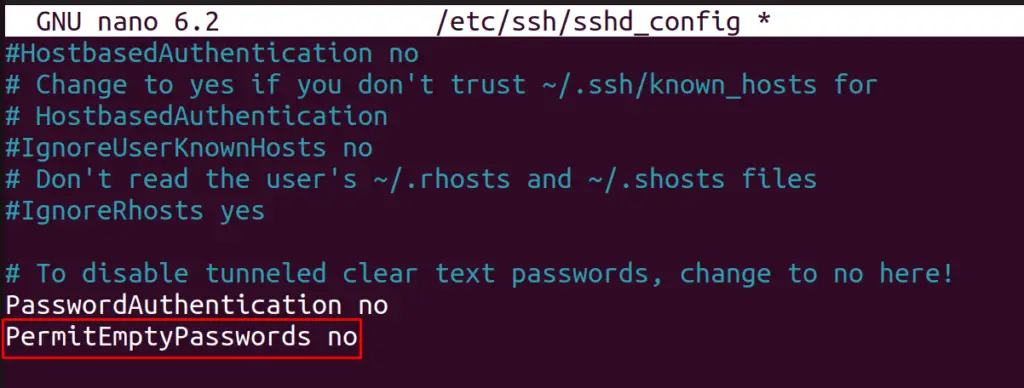
Disable the empty password acceptance feature of the SSH. For this, look for the line “PermitEmptyPasswords”, remove the “#” from the line, and set its value to “no”:
Step 8: Configure the Client TimeOut Session
Set the time limit so that, if the client remains inactive for specific seconds, the connection will automatically be terminated.
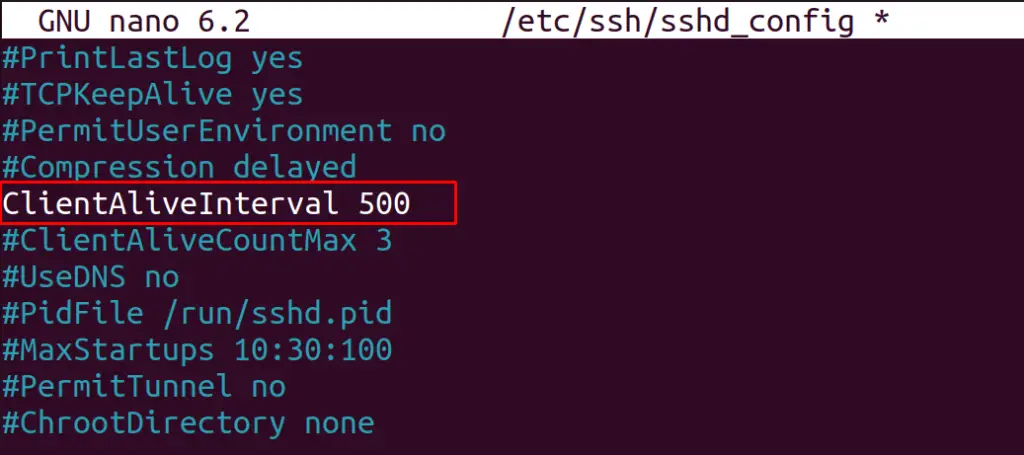
For this, trace the line “ClientAliveIntervalLine”, uncomment it and write a specific value in seconds as we did here:
Step 9: Use Protocol 2
Next step is to change the SSH protocol as SSH can work on two types of protocols; Protocol 1, and Protocol 2. Protocol 2 is a more advanced and secure protocol than Protocol 1.
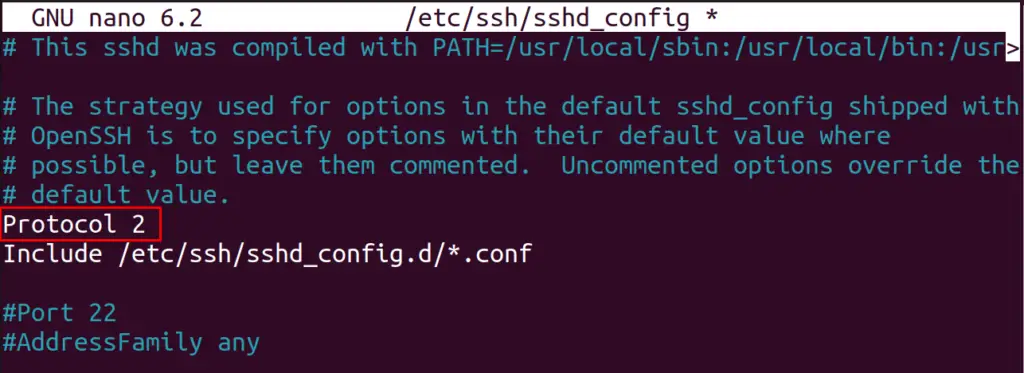
For this, add the following line to the file:
Protocol 2
Note: All the above steps can be performed in any order. There is no restriction on the execution order of these steps.
Moreover, the “sshd_config” file is enriched with various options that can be configured per the user’s requirement.
Once you are done with the configuration, it is recommended to restart these services via the following command:
$ sudo systemctl restart sshd
The SSH server is fully secured on a basic level.
Conclusion
To secure the SSH server in Ubuntu, open the configuration file of the SSH by running the command “sudo nano /etc/ssh/sshd_config” in the terminal. This file can be accessed to configure tens of parameters that are supposed to secure the SSH server in Ubuntu 22.04.
