The nmap tool is an open-source, free network scanner that can discover hosts and services on a system by analyzing the response received from the network packets it sends. The nmap allows users to map networks and discover online hosts that can be used to detect vulnerable ports and services on a specific network or ports.
This write-up will guide you about the scanning of services and vulnerabilities with the nmap tool with the help of useful examples. The supporting content is as follows:
- How to Scan for Services and Vulnerabilities with Nmap?
- Basic Scan for Services with Nmap
- Scan for Vulnerabilities with NSE (Nmap Script Engine)
- Scan for Services and Vulnerabilities with Nmap Vulners
- Scan for Services and Vulnerabilities with Nmap Vulscan
- Scan for Services and Vulnerabilities with Nmap Vuln
How to Scan for Services and Vulnerabilities With Nmap?
The nmap command can detect open ports and the services running on a host. It can be used to identify vulnerabilities and specific services on one or multiple hosts on a network.
Basic Scan for Services with Nmap
First have a look at the general syntax of the nmap command:
$ nmap scan-type <options> target-destination
The above command explanation is as follows:
- scan-type: The specific network protocol can be scanned by putting its option here. For example, “PS” for TCP scan and “PU” for UDP scan.
- options: The nmap command available option is added here that performs the specific task.
- target-destination: Replace it with the target host IP or network address.
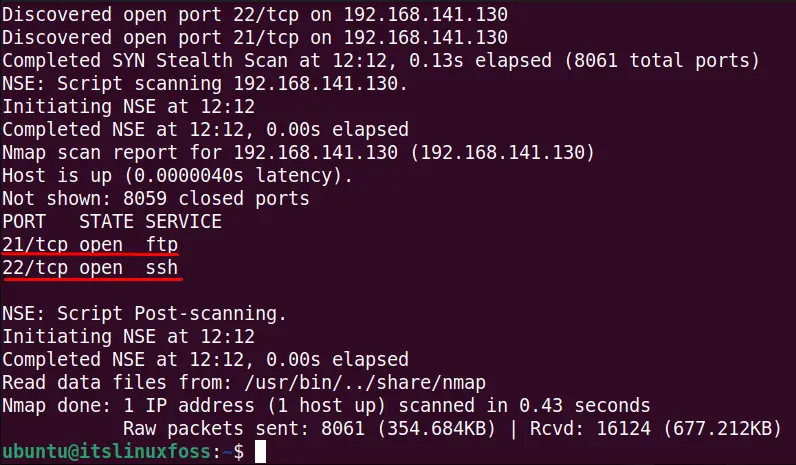
To scan for the open ports and services with the nmap command for a specific host having IP address “192.168.141.130”, run this command:
$ nmap 192.168.141.130
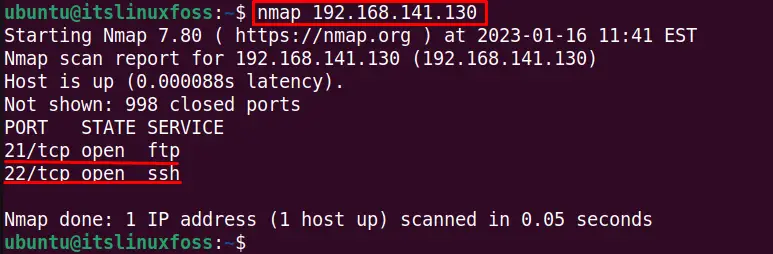
The ports 21 and 22 have their respective running services (ftp and ssh) opened in the output.
To detect the opened ports and services for a network (in this case, www.google .com), use the below-stated command:
$ nmap www.google.com
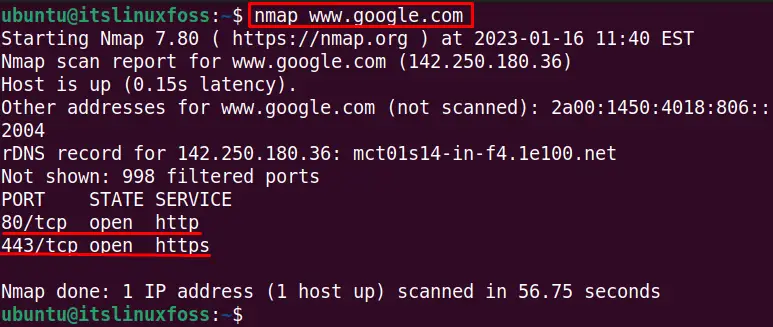
Two ports are opened with HTTP and HTTPS services running on the opened ports.
The “script=banner” option is used with the nmap command to detect the services opened in the system for a specific IP address, as shown below:
$ nmap --script=banner 192.168.141.130
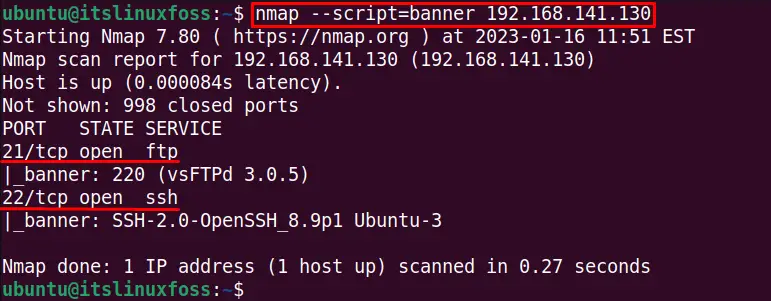
The output shows that vsFTP and OpenSSH services are used for the opened ports.
Scan for Vulnerabilities With NSE (Nmap Script Engine)
The nmap tool includes several scripts to scan the vulnerabilities and services. This section will discuss three NSE built-in scripts to scan the vulnerabilities, while the users can write customized scripts.
Before using the nmap scripts, it’s recommended to update the scripts database to the newest version with the following command:
$ sudo nmap --script-updatedb
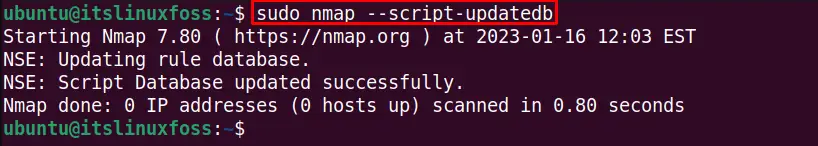
The nmap scripts are updated.
Scan for Services and Vulnerabilities with Nmap Vulners
The nmap vulners script can be used in different ways to find the services and their vulnerabilities for the hosts and ports. In Linux, the vulners script exists in the default nmap scripts directory “/usr/share/nmap”, which can be verified if the NSE is available in the system with the following command:
$ ls -al /usr/share/nmap/ scripts/ | grep -e "vulners"
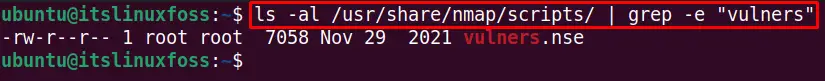
The vulners script is available in nmap scripts database.
The nmap vulners scripts scan for services and vulnerabilities for a specific port. For example, the below command is used with the sV option of the nmap command that shows the version of the running services to detect the vulnerabilities on a single port:
$ sudo nmap -sV -v --script vulners 192.168.141.130
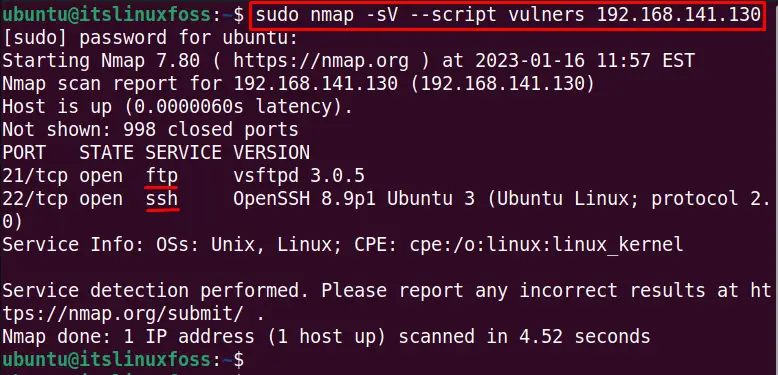
The output shows the two services “ftp”, and “ssh” is running on the services while no vulnerabilities are shown in the output. In our case, the vulnerability can be seen.
To scan for vulnerabilities and services for specific ports from 20 to 8080 with the nmap vulners, run the below-stated command:
$ sudo nmap -sV -p20-8080 --script vulners 192.168.141.130
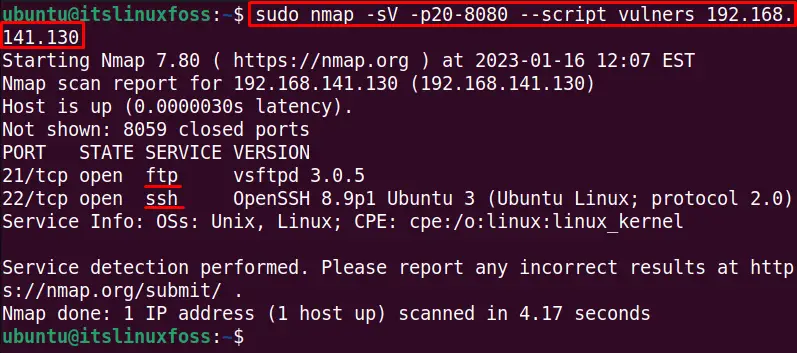
No vulnerability is shown in the output.
To check more details about the nmap vulners scanning, we can use the “v” verbose option to check the details as shown below:
$ sudo nmap -v -p20-8080 --script vulners 192.168.141.130
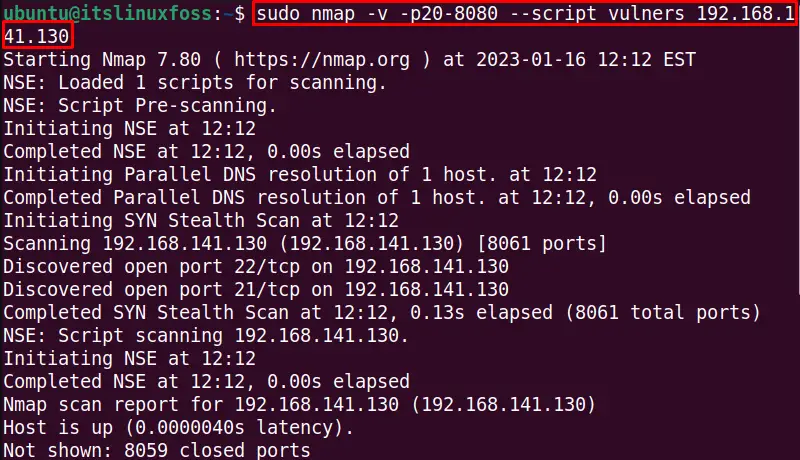
The below output also shows the nmap vulnerability scanning details:
Scan for Services and Vulnerabilities With Nmap Vulscan
The vulscan in another nmap script can be used to check for services and vulnerabilities for the online hosts. The vulscan is not installed by default in the nmap tool, and to install the vulscan, use the below steps:
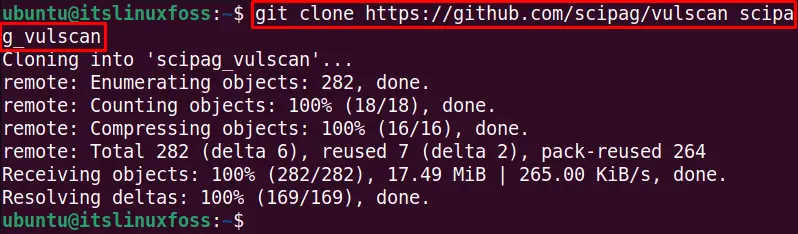
- Make the vulscan git repository clone in the system with the following command:
$ git clone https://github.com/scipag/vulscan scipag_vulscan
- Make the soft link of git clone vulscan to the default nmap scripts directory with the following command:
$ ln -s `pwd`/scipag_vulscan /usr/share/nmap/scripts/vulscan
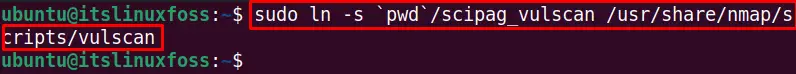
The vulscan is installed in the system and linked to the default repository.
To scan the host with IP address “192.168.141.130” for the vulnerability, use the below-stated command:
$ nmap -sV --script=vulscan/vulscan.nse 192.168.141.130
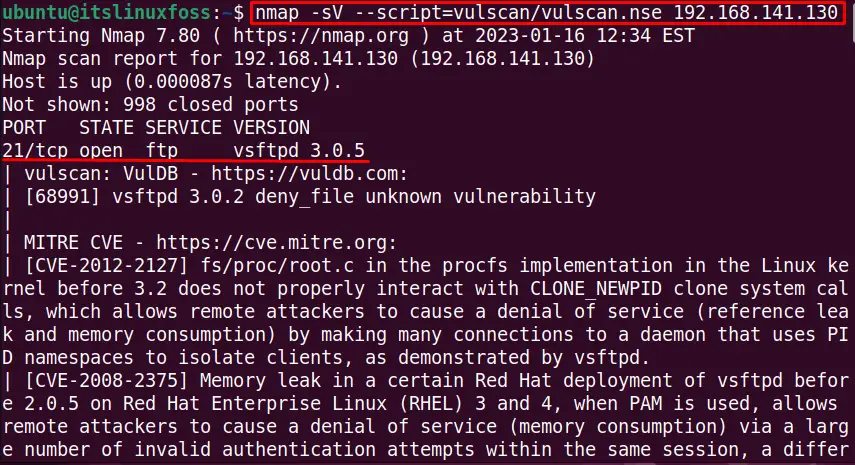
The output shows the opened ports for the host and detects the vulnerability:
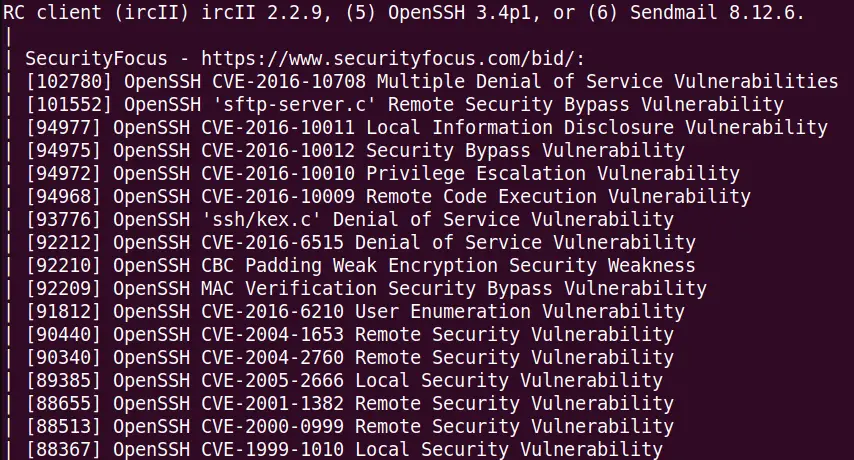
To scan the services and vulnerability for a particular port (in this case, port 22), execute this command:
$ nmap -sV -p22 --script=vulscan/vulscan.nse 192.168.141.130
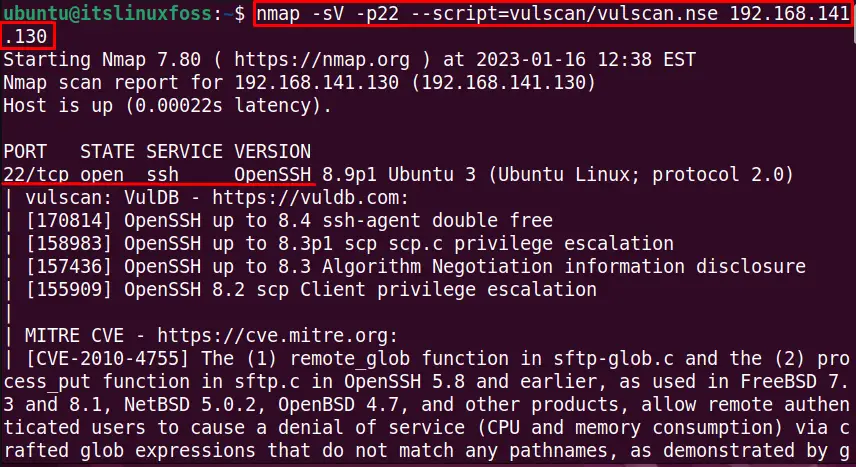
The output shows that port 22 is opened and lists the vulnerabilities while scanning (the output shows a long list of vulnerabilities).
Similarly, we can do the vulnerability scan for multiple hosts with their IP addresses. The below performs the scan for services and vulnerability with nmap vulscan for two hosts:
$ nmap -sV --script=vulscan/vulscan.nse 192.168.141.130 192.168.141.129
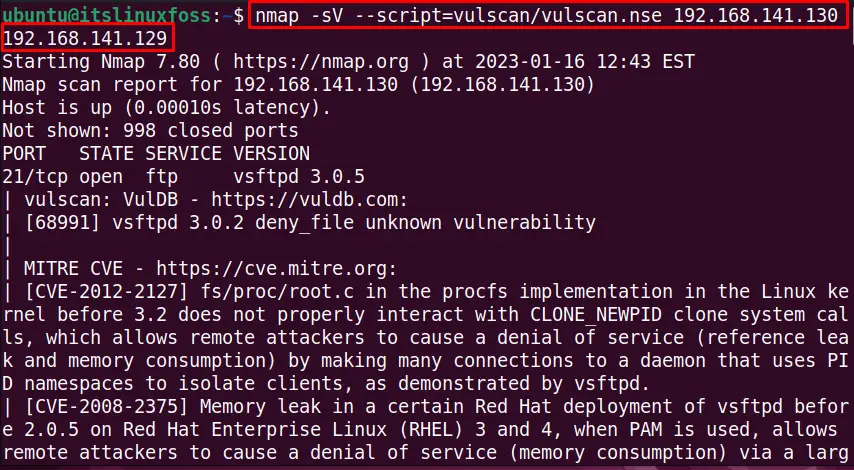
The output shows the opened services for both hosts and vulnerabilities.
Scan for Services and Vulnerabilities With Nmap Vuln
The nmap vuln script can also be used to scan the services and vulnerabilities in Linux for a specific port, multiple ports, subdomains of the ports, and the range of ports. For example, the below command detects the services and vulnerabilities for the host IP “192.168.141.130” by using the nmap vulscan:
$ sudo nmap --script vuln 192.168.141.130 -V
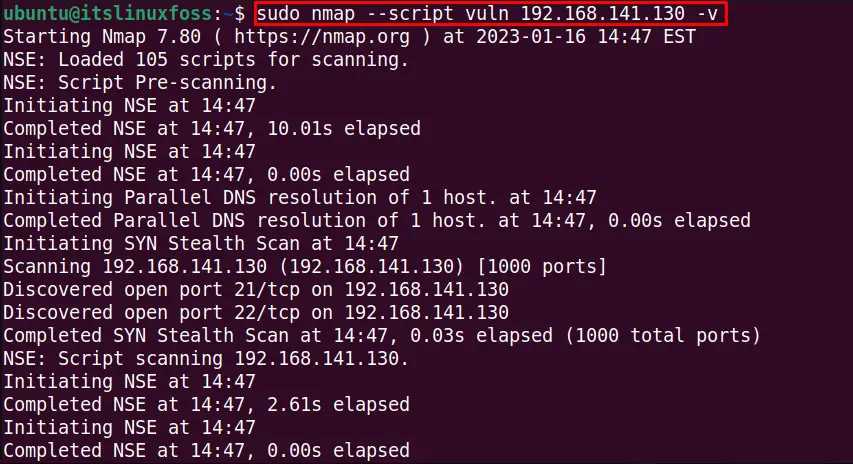
The output displays the scanning details about the services and vulnerabilities with the nmap vulscan while there is no vulnerability detected:
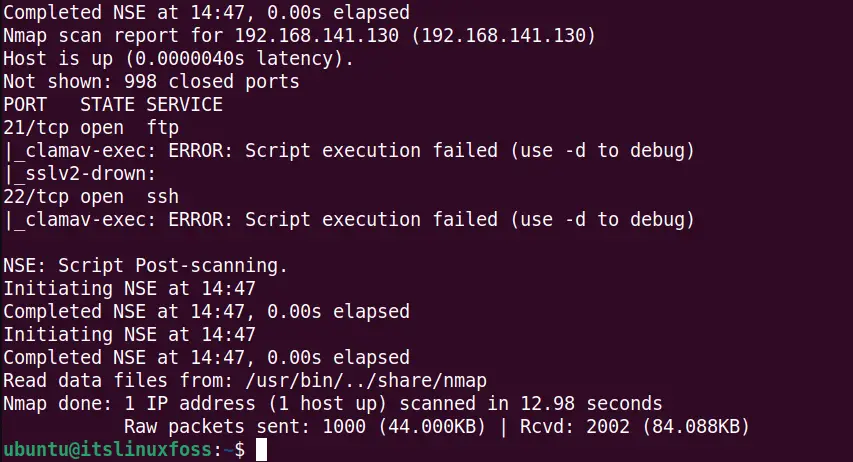
The full subnet range can be scanned with then nmap to detect the open ports, services, and vulnerabilities using this command:
$ sudo nmap --script vuln 192.168.141.*
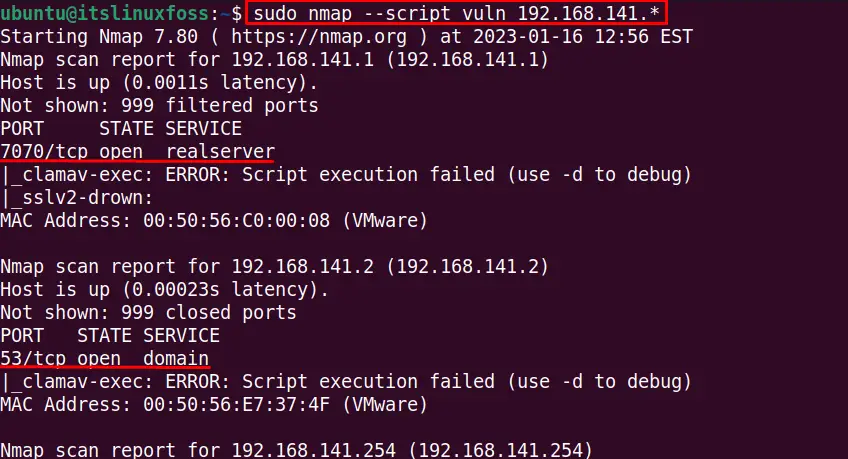
These are useful methods to scan for services and vulnerabilities with the nmap.
Conclusion
The Nmap scripts can be used to scan the services and vulnerabilities in Linux. The nmap tool is flexible and comes with many advanced features which can scan for vulnerabilities in a specific port, multiple ports, and the range of a port, as performed with examples in the write-up.
